Passleader offers free demo for 312-50v11 exam. "Certified Ethical Hacker Exam (CEH v11)", also known as 312-50v11 exam, is a EC-Council Certification. This set of posts, Passing the EC-Council 312-50v11 exam, will help you answer those questions. The 312-50v11 Questions & Answers covers all the knowledge points of the real exam. 100% real EC-Council 312-50v11 exams and revised by experts!
Free 312-50v11 Demo Online For EC-Council Certifitcation:
NEW QUESTION 1
What type of analysis is performed when an attacker has partial knowledge of inner-workings of the application?
- A. Black-box
- B. Announced
- C. White-box
- D. Grey-box
Answer: D
NEW QUESTION 2
By using a smart card and pin, you are using a two-factor authentication that satisfies
- A. Something you are and something you remember
- B. Something you have and something you know
- C. Something you know and something you are
- D. Something you have and something you are
Answer: B
NEW QUESTION 3
What is the main security service a cryptographic hash provides?
- A. Integrity and ease of computation
- B. Message authentication and collision resistance
- C. Integrity and collision resistance
- D. Integrity and computational in-feasibility
Answer: D
NEW QUESTION 4
Why containers are less secure that virtual machines?
- A. Host OS on containers has a larger surface attack.
- B. Containers may full fill disk space of the host.
- C. A compromise container may cause a CPU starvation of the host.
- D. Containers are attached to the same virtual network.
Answer: A
NEW QUESTION 5
What does the –oX flag do in an Nmap scan?
- A. Perform an eXpress scan
- B. Output the results in truncated format to the screen
- C. Output the results in XML format to a file
- D. Perform an Xmas scan
Answer: C
NEW QUESTION 6
You are attempting to crack LM Manager hashed from Windows 2000 SAM file. You will be using LM Brute force hacking tool for decryption. What encryption algorithm will you be decrypting?
- A. MD4
- B. DES
- C. SHA
- D. SSL
Answer: B
NEW QUESTION 7
Which of the following is an extremely common IDS evasion technique in the web world?
- A. Spyware
- B. Subnetting
- C. Unicode Characters
- D. Port Knocking
Answer: C
NEW QUESTION 8
You are the Network Admin, and you get a complaint that some of the websites are no longer accessible. You try to ping the servers and find them to be reachable. Then you type the IP address and then you try on the browser, and find it to be accessible. But they are not accessible when you try using the URL.
What may be the problem?
- A. Traffic is Blocked on UDP Port 53
- B. Traffic is Blocked on TCP Port 80
- C. Traffic is Blocked on TCP Port 54
- D. Traffic is Blocked on UDP Port 80
Answer: A
NEW QUESTION 9
Which of the following is the BEST way to defend against network sniffing?
- A. Using encryption protocols to secure network communications
- B. Register all machines MAC Address in a Centralized Database
- C. Use Static IP Address
- D. Restrict Physical Access to Server Rooms hosting Critical Servers
Answer: A
NEW QUESTION 10
What is the algorithm used by LM for Windows2000 SAM?
- A. MD4
- B. DES
- C. SHA
- D. SSL
Answer: B
NEW QUESTION 11
Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?
- A. ESP transport mode
- B. ESP confidential
- C. AH permiscuous
- D. AH Tunnel mode
Answer: A
NEW QUESTION 12
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
- A. 137 and 139
- B. 137 and 443
- C. 139 and 443
- D. 139 and 445
Answer: D
NEW QUESTION 13
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
- A. Encrypt the Sales.xls using PGP and e-mail it to your personal gmail account
- B. Package the Sales.xls using Trojan wrappers and telnet them back your home computer
- C. You can conceal the Sales.xls database in another file like photo.jpg or other files and send it out in an innocent looking email or file transfer using Steganography techniques
- D. Change the extension of Sales.xls to sales.txt and upload them as attachment to your hotmail account
Answer: C
NEW QUESTION 14
Internet Protocol Security IPsec is actually a suite pf protocols. Each protocol within the suite provides different functionality. Collective IPsec does everything except.
- A. Protect the payload and the headers
- B. Encrypt
- C. Work at the Data Link Layer
- D. Authenticate
Answer: D
NEW QUESTION 15
Which of the following are well known password-cracking programs?
- A. L0phtcrack
- B. NetCat
- C. Jack the Ripper
- D. Netbus
- E. John the Ripper
Answer: AE
NEW QUESTION 16
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c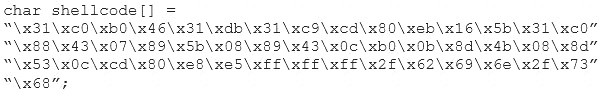
What is the hexadecimal value of NOP instruction?
- A. 0x60
- B. 0x80
- C. 0x70
- D. 0x90
Answer: D
NEW QUESTION 17
While examining audit logs, you discover that people are able to telnet into the SMTP server on port 25. You would like to block this, though you do not see any evidence of an attack or other wrong doing. However, you are concerned about affecting the normal functionality of the email server. From the following options choose how best you can achieve this objective?
- A. Block port 25 at the firewall.
- B. Shut off the SMTP service on the server.
- C. Force all connections to use a username and password.
- D. Switch from Windows Exchange to UNIX Sendmail.
- E. None of the above.
Answer: E
NEW QUESTION 18
Which of the following DoS tools is used to attack target web applications by starvation of available sessions on the web server?
The tool keeps sessions at halt using never-ending POST transmissions and sending an arbitrarily large content-length header value.
- A. My Doom
- B. Astacheldraht
- C. R-U-Dead-Yet?(RUDY)
- D. LOIC
Answer: C
NEW QUESTION 19
“........is an attack type for a rogue Wi-Fi access point that appears to be a legitimate one offered on the premises, but actually has been set up to eavesdrop on wireless communications. It is the wireless version of the phishing scam. An attacker fools wireless users into connecting a laptop or mobile phone to a tainted hot-spot by posing as a legitimate provider. This type of attack may be used to steal the passwords of
unsuspecting users by either snooping the communication link or by phishing, which involves setting up a fraudulent web site and luring people there.”
Fill in the blank with appropriate choice.
- A. Evil Twin Attack
- B. Sinkhole Attack
- C. Collision Attack
- D. Signal Jamming Attack
Answer: A
NEW QUESTION 20
What is the proper response for a NULL scan if the port is open?
- A. SYN
- B. ACK
- C. FIN
- D. PSH
- E. RST
- F. No response
Answer: F
NEW QUESTION 21
What is the proper response for a NULL scan if the port is closed?
- A. SYN
- B. ACK
- C. FIN
- D. PSH
- E. RST
- F. No response
Answer: E
NEW QUESTION 22
When purchasing a biometric system, one of the considerations that should be reviewed is the processing speed. Which of the following best describes what it is meant by processing?
- A. The amount of time and resources that are necessary to maintain a biometric system
- B. How long it takes to setup individual user accounts
- C. The amount of time it takes to be either accepted or rejected from when an individual provides identification and authentication information
- D. The amount of time it takes to convert biometric data into a template on a smart card
Answer: C
NEW QUESTION 23
You need a tool that can do network intrusion prevention and intrusion detection, function as a network sniffer, and record network activity, what tool would you most likely select?
- A. Nmap
- B. Cain & Abel
- C. Nessus
- D. Snort
Answer: D
NEW QUESTION 24
A network admin contacts you. He is concerned that ARP spoofing or poisoning might occur on his network. What are some things he can do to prevent it? Select the best answers.
- A. Use port security on his switches.
- B. Use a tool like ARPwatch to monitor for strange ARP activity.
- C. Use a firewall between all LAN segments.
- D. If you have a small network, use static ARP entries.
- E. Use only static IP addresses on all PC's.
Answer: ABD
NEW QUESTION 25
......
Thanks for reading the newest 312-50v11 exam dumps! We recommend you to try the PREMIUM Downloadfreepdf.net 312-50v11 dumps in VCE and PDF here: https://www.downloadfreepdf.net/312-50v11-pdf-download.html (254 Q&As Dumps)
