Exam Code: 70-411 (70 411 study guide), Exam Name: Administering Windows Server 2012, Certification Provider: Microsoft Certifitcation, Free Today! Guaranteed Training- Pass 70-411 Exam.
Also have 70-411 free dumps questions for you:
NEW QUESTION 1
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Network Policy Server server role installed.
You need to allow connections that use 802.1x. What should you create?
- A. A network policy that uses Microsoft Protected EAP (PEAP) authentication
- B. A network policy that uses EAP-MSCHAP v2 authentication
- C. A connection request policy that uses EAP-MSCHAP v2 authentication
- D. A connection request policy that uses MS-CHAP v2 authentication
Answer: C
Explanation: 802.1X uses EAP, EAP-TLS, EAP-MS-CHAP v2, and PEAP authentication methods:
✑ EAP (Extensible Authentication Protocol) uses an arbitrary authentication method, such as certificates, smart cards, or credentials.
✑ EAP-TLS (EAP-Transport Layer Security) is an EAP type that is used in certificate- based security environments, and it provides the strongest authentication and key determination method.
✑ EAP-MS-CHAP v2 (EAP-Microsoft Challenge Handshake Authentication Protocol version 2) is a mutual authentication method that supports password-based user or computer authentication.
✑ PEAP (Protected EAP) is an authentication method that uses TLS to enhance the security of other EAP authentication protocols.
Connection request policies are sets of conditions and settings that allow network administrators to designate which Remote Authentication Dial-In User Service (RADIUS) servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients. Connection request policies can be configured to designate which RADIUS servers are used for RADIUS accounting.
With connection request policies, you can use NPS as a RADIUS server or as a RADIUS proxy, based on factors such as the following:
✑ The time of day and day of the week
✑ The realm name in the connection request
✑ The type of connection being requested
✑ The IP address of the RADIUS client
NEW QUESTION 2
Your network contains an Active Directory domain named contoso.com. The domain contains five servers. The servers are configured as shown in the following table.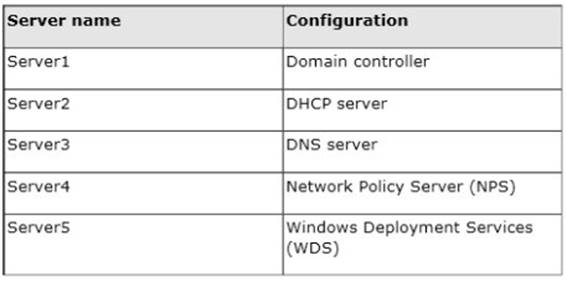
All desktop computers in contoso.com run Windows 8 and are configured to use BitLocker Drive Encryption (BitLocker) on all local disk drives.
You need to deploy the Network Unlock feature. The solution must minimize the number of features and server roles installed on the network.
To which server should you deploy the feature?
- A. Server1
- B. Server2
- C. Server3
- D. Server4
- E. Server5
Answer: E
Explanation: The BitLocker Network Unlock feature will install the WDS role if it is not already installed. If you want to install it separately before you install BitLocker Network Unlock you can use Server Manager or Windows PowerShell. To install the role using Server Manager, select the Windows Deployment Services role in Server Manager.
NEW QUESTION 3
You have a server named Server 1.
You enable BitLocker Drive Encryption (BitLocker) on Server 1.
You need to change the password for the Trusted Platform Module (TPM) chip. What should you run on Server1?
- A. Manage-bde.exe
- B. Set-TpmOwnerAuth
- C. bdehdcfg.exe
- D. tpmvscmgr.exe
Answer: B
Explanation: The Set-TpmOwnerAuthcmdlet changes the current owner authorization value of the Trusted Platform Module (TPM) to a new value. You can specify the current owner authorization value or specify a file that contains the current owner authorization value. If you do not specify an owner authorization value, the cmdlet attempts to read the value from the registry.
Use the ConvertTo-TpmOwnerAuthcmdlet to create an owner authorization value. You can specify a new owner authorization value or specify a file that contains the new value.
NEW QUESTION 4
DRAG DROP
Your network contains a production Active Directory forest named contoso.com and a test Active Directory forest named test.contoso.com. There is no network connectivity between contoso.com and test.contoso.com.
The test.contoso.com domain contains a Group Policy object (GPO) named GPO1. You need to apply the settings in GPO1 to the contoso.com domain.
Which four actions should you perform?
To answer, move the four appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Answer:
Explanation: 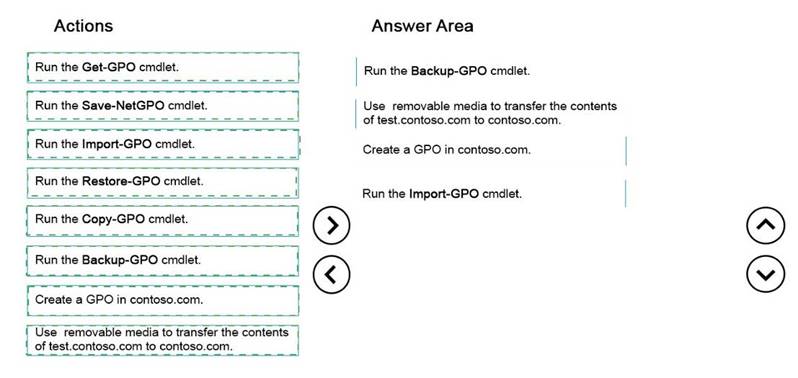
NEW QUESTION 5
CORRECT TEXT
You have a server named Server1 that is a number of a domain named contoso.com. You view the properties of a service on Server1 as shown in the graphic.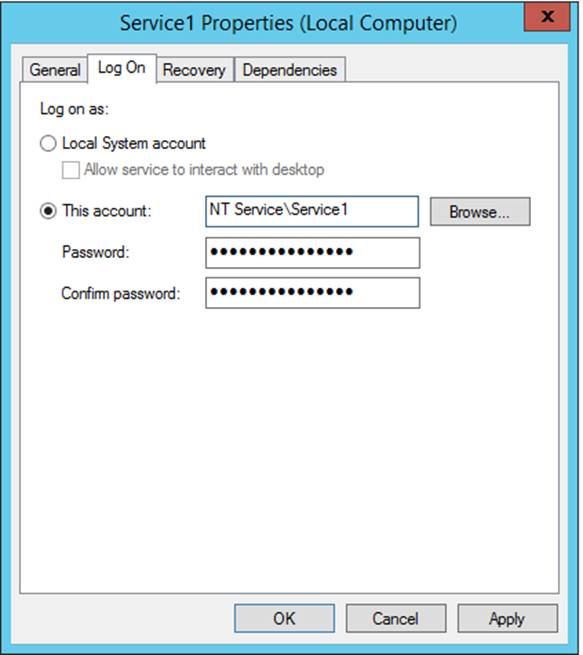
Use the drop-down menus to select the answer choice that completes each statement. NOTE: Each correct selection is worth one point.
Answer:
Explanation: 
References:
https://msdn.microsoft.com/en-us/library/ms677272(v=vs.85).aspx https://msdn.microsoft.com/en-us/library/ms675915(v=vs.85).aspx
Virtual accounts are "managed local accounts" that provide the following features to simplify service administration:
- No password management is required.
- The ability to access the network with a computer identity in a domain environment.
Virtual accounts require very little management. They cannot be created or deleted, nor do they require any password management.
You must be a member of the Administrators group on the local computer to perform the following procedures. To configure a service to use a virtual account:
- Click Start, point to Administrative Tools, and then click Services.
- In the details pane, right-click the service that you want to configure, and then click Properties.
- Click the Log On tab, click This account, and then type NT SERVICEServiceName.
When you are finished, click OK.
- Restart the service for the change to take effect. https://technet.microsoft.com/en-us/library/dd548356%20(v=WS.10).aspx
NEW QUESTION 6
Your network contains an Active Directory forest named contoso.com. The functional level of the forest is Windows Server 2008 R2.
All of the user accounts in the marketing department are members of a group named ContosoMarketingUsers. All of the computer accounts in the marketing department are members of a group named ContosoMarketingComputers.
A domain user named User1 is a member of the ContosoMarketingUsers group. A computer named Computer1 is a member of the ContosoMarketingComputers group.
You have four Password Settings objects (PSOs). The PSOs are defined as shown in the following table.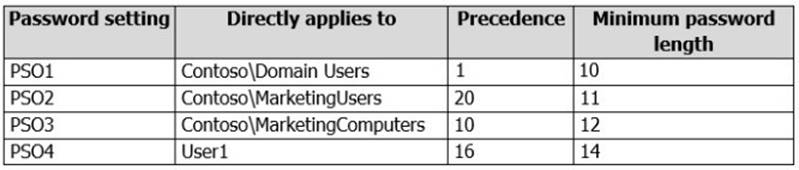
When User1 logs on to Computer1 and attempts to change her password, she receives an error message indicating that her password is too short.
You need to tell User1 what her minimum password length is. What should you tell User1?
- A. 10
- B. 11
- C. 12
- D. 14
Answer: D
NEW QUESTION 7
Your network contains a single Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that hosts the primary DNS zone for contoso.com.
All servers dynamically register their host names.
You install two new Web servers that host identical copies of your company's intranet website. The servers are configured as shown in the following table.
You need to use DNS records to load balance name resolution queries for intranet.contoso.com between the three Web servers.
What is the minimum number of DNS records that you should create manually?
- A. 1
- B. 2
- C. 3
- D. 4
Answer: B
NEW QUESTION 8
Your network contains two servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
On Server1, you create a Data Collector Set (DCS) named Data1. You need to export Data1 to Server2.
What should you do first?
- A. Right-click Data1 and click Data Manager.
- B. Right-click Data1 and click Export list.
- C. Right-click Data1 and click Properties.
- D. Right-click Data1 and click Save template.
Answer: D
NEW QUESTION 9
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2.
An organizational unit (OU) named ResearchServers contains the computer accounts of all research servers.
All domain users are configured to have a minimum password length of eight characters. You need to ensure that the minimum password length of the local user accounts on the
research servers in the ResearchServers OU is 10 characters.
What should you do?
- A. Configure a local Group Policy object (GPO) on each research server.
- B. Create and link a Group Policy object (GPO) to the ResearchServers OU.
- C. Create a universal group that contains the research server
- D. Create a Password Settings object (PSO) and assign the PSO to the group.
- E. Create a global group that contains the research server
- F. Create a Password Settings object (PSO) and assign the PSO to the group.
Answer: B
Explanation: For a domain, and you are on a member server or a workstation that is joined to the domain
1. Open Microsoft Management Console (MMC).
2. On the File menu, click Add/Remove Snap-in, and then click Add.
3. Click Group Policy Object Editor, and then click Add.
4. In Select Group Policy Object, click Browse.
5. In Browse for a Group Policy Object, select a Group Policy object (GPO) in the appropriate domain, site, or organizational unit--or create a new one, click OK, and then click Finish.
6. Click Close, and then click OK.
7. In the console tree, click Password Policy. Where?
Group Policy Object [computer name] Policy/Computer Configuration/Windows Settings/Security Settings/Account Policies/Password Policy
8. In the details pane, right-click the policy setting that you want, and then click Properties.
9. If you are defining this policy setting for the first time, select the Define this policy setting check box.
10. Select the options that you want, and then click OK.
NEW QUESTION 10
You have a file server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager role service installed.
Files created by users in the human resources department are assigned the Department classification property automatically.
You are configuring a file management task named Task1 to remove user files that have not been accessed for 60 days or more.
You need to ensure that Task1 only removes files that have a Department classification property of human resources. The solution must minimize administrative effort.
What should you configure on Task1?
- A. Configure a file screen
- B. Create a condition
- C. Create a classification rule
- D. Create a custom action
Answer: B
Explanation: Create a File Expiration Task
The following procedure guides you through the process of creating a file management task for expiring files. File expiration tasks are used to automatically move all files that match certain criteria to a specified expiration directory, where an administrator can then back those files up and delete them. Property conditions. Click Add to create a new condition based on the file’s classification. This will open the Property Condition dialog box, which allows you to select a property, an operator to perform on the property, and the value to compare the property against. After clicking OK, you can then create additional conditions, or edit or remove an existing condition.
NEW QUESTION 11
HOTSPOT
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The forest contains two Active Directory sites named Site1 and Site2.
You plan to deploy a read-only domain controller (RODC) named DC10 to Site2. You pre- create the DC10 domain controller account by using Active Directory Users and Computers.
You need to identify which domain controller will be used for initial replication during the promotion of the RODC.
Which tab should you use to identify the domain controller? To answer, select the appropriate tab in the answer area.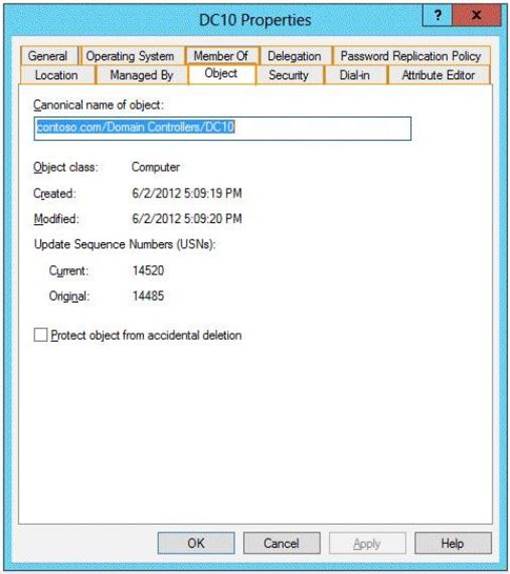
Answer:
Explanation: 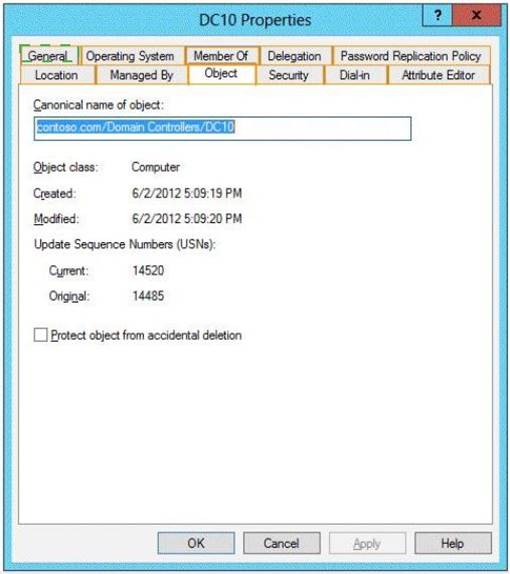
NEW QUESTION 12
Your network contains a single Active Directory domain named contoso.com. The domain contains a member server named Server1 that runs Windows Server 2012 R2.
Server1 has the Windows Server updates Services server role installed and is configured to download updates from the Microsoft Update servers.
You need to ensure that Server1 downloads express installation files from the Microsoft Update servers.
What should you do from the Update Services console?
- A. From the Update Files and Languages options, configure the Update Files settings.
- B. From the Automatic Approvals options, configure the Update Rules settings.
- C. From the Products and Classifications options, configure the Products settings.
- D. From the Products and Classifications options, configure the Classifications settings.
Answer: A
Explanation: To specify whether express installation files are downloaded during synchronization In the left pane of the WSUS Administration console, click Options.
In Update Files and Languages, click the Update Files tab.
If you want to download express installation files, select the Download express installation files check box. If you do not want to download express installation files, clear the check box.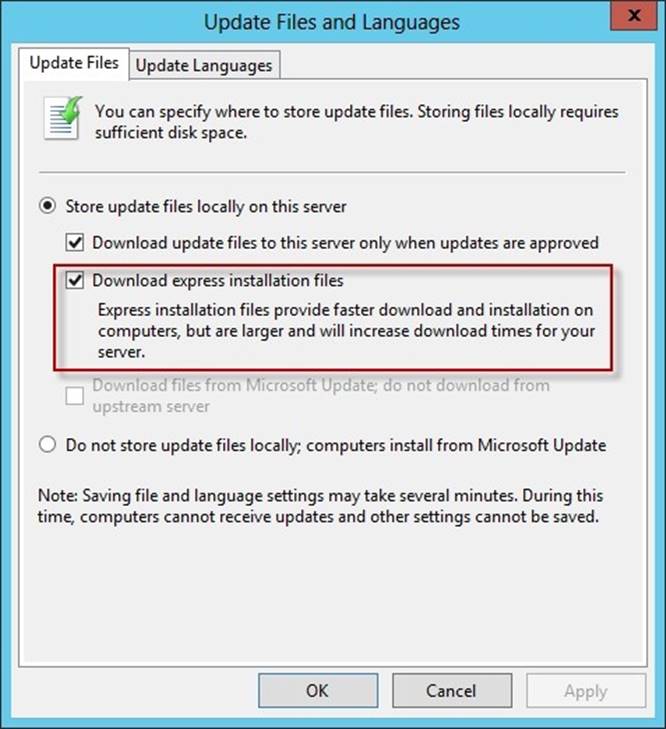
Reference:
http: //technet. microsoft. com/en-us/library/cc708431. aspx
http: //technet. microsoft.com/en-us/library/cc708431. aspx
NEW QUESTION 13
Your network contains an Active Directory domain named adatum.com. The domain
contains a server named Server1 that runs Windows Server 2012 R2. Server1 is configured as a Network Policy Server (NPS) server and as a DHCP server.
The network contains two subnets named Subnet1 and Subnet2. Server1 has a DHCP scope for each subnet.
You need to ensure that noncompliant computers on Subnet1 receive different network policies than noncompliant computers on Subnet2.
Which two settings should you configure? (Each correct answer presents part of the solution. Choose two.)
- A. The NAP-Capable Computers conditions
- B. The NAS Port Type constraints
- C. The Health Policies conditions
- D. The MS-Service Class conditions
- E. The Called Station ID constraints
Answer: CD
Explanation: The NAP health policy server uses the NPS role service with configured health policies and system health validators (SHVs) to evaluate client health based on administrator-defined requirements. Based on results of this evaluation, NPS instructs the DHCP server to provide full access to compliant NAP client computers and to restrict access to client computers that are noncompliant with health requirements.
If policies are filtered by DHCP scope, then MS-Service Class is configured in policy conditions.
NEW QUESTION 14
DRAG DROP
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Network Policy and Access Services server role installed.
All of the VPN servers on your network use Server1 for RADIUS authentication. You create a security group named Group1.
You need to configure Network Policy and Access Services (NPAS) to meet the following requirements:
✑ Ensure that only the members of Group1 can establish a VPN connection to the VPN servers.
✑ Allow only the members of Group1 to establish a VPN connection to the VPN
servers if the members are using client computers that run Windows 8 or later. Which type of policy should you create for each requirement?
To answer, drag the appropriate policy types to the correct requirements. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Answer:
Explanation: 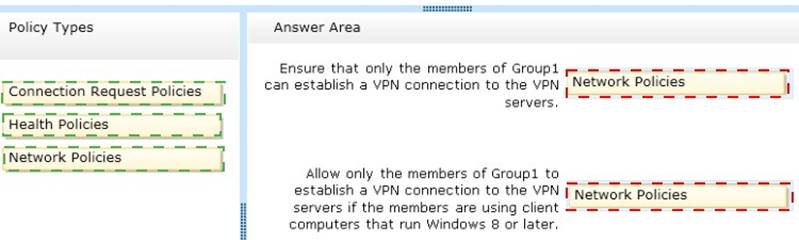
NEW QUESTION 15
You have a cluster named Cluster1 that contains two nodes. Both nodes run Windows Server 2012 R2. Cluster1 hosts a virtual machine named VM1 that runs Windows Server 2012 R2.
You configure a custom service on VM1 named Service1.
You need to ensure that VM1 will be moved to a different node if Service1 fails. Which cmdlet should you run on Cluster1?
- A. Add-ClusterVmMonitoredItem
- B. Add-ClusterGenericServiceRole
- C. Set-ClusterResourceDependency
- D. Enable VmResourceMetering
Answer: A
Explanation: The Add-ClusterVMMonitoredItem cmdlet configures monitoring for a service or an Event Tracing for Windows (ETW) event so that it is monitored on a virtual machine. If the service fails or the event occurs, then the system responds by taking an action based on the failover configuration for the virtual machine resource. For example, the configuration might specify that the virtual machine be restarted.
Topic 3, Exam Set C (NEW)
NEW QUESTION 16
Your network contains an Active Directory domain named adatum.com. All domain controllers run Windows Server 2012 R2. The domain contains a virtual machine named DC2.
On DC2, you run Get-ADDCCIoningExcludedApplicationList and receive the output shown in the following table.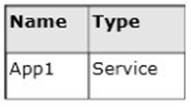
You need to ensure that you can clone DC2.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)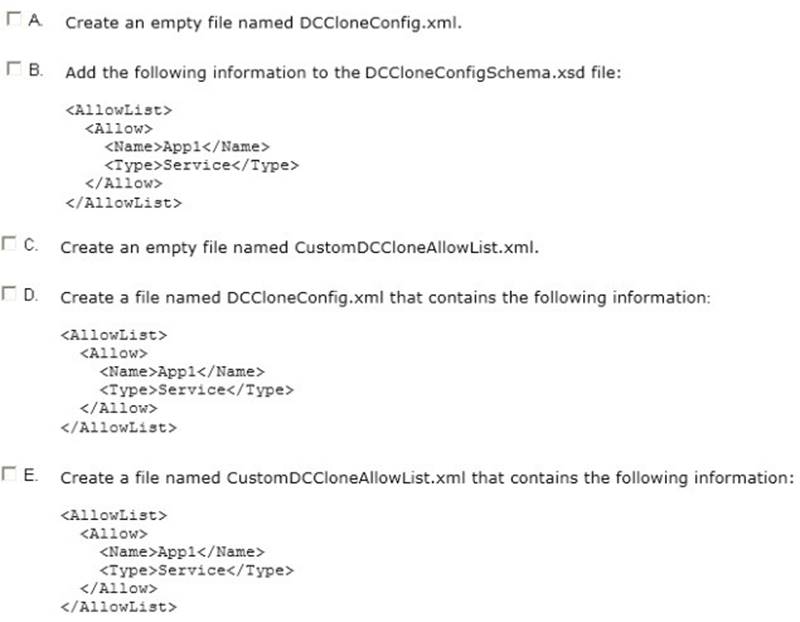
- A. Option A
- B. Option B
- C. Option C
- D. Option D
- E. Option E
Answer: AE
Explanation: Because domain controllers provide a distributed environment, you could not safely clone an Active Directory domain controller in the past.
Before, if you cloned any server, the server would end up with the same domain or forest, which is unsupported with the same domain or forest. You would then have to run sysprep, which would remove the unique security information before cloning and then promote a domain controller manually. When you clone a domain controller, you perform safe cloning, which a cloned domain controller automatically runs a subset of the sysprep process and promotes the server to a domain controller automatically.
The four primary steps to deploy a cloned virtualized domain controller are as follows:
✑ Grant the source virtualized domain controller the permission to be cloned by adding the source virtualized domain controller to the Cloneable Domain Controllers group.
✑ Run Get-ADDCCloningExcludedApplicationListcmdlet in Windows PowerShell to determine which services and applications on the domain controller are not compatible with the cloning.
✑ Run New-ADDCCloneConfigFile to create the clone configuration file, which is
stored in the C:WindowsNTDS.
✑ In Hyper-V, export and then import the virtual machine of the source domain controller.
Run Get-ADDCCloningExcludedApplicationListcmdlet In this procedure, run the Get- ADDCCloningExcludedApplicationListcmdlet on the source virtualized domain controller to identify any programs or services that are not evaluated for cloning. You need to run the Get-ADDCCloningExcludedApplicationListcmdlet before the New- ADDCCloneConfigFilecmdlet because if the New-ADDCCloneConfigFilecmdlet detects an excluded application, it will not create a DCCloneConfig.xml file. To identify applications or services that run on a source domain controller which have not been evaluated for cloning. Get-ADDCCloningExcludedApplicationList
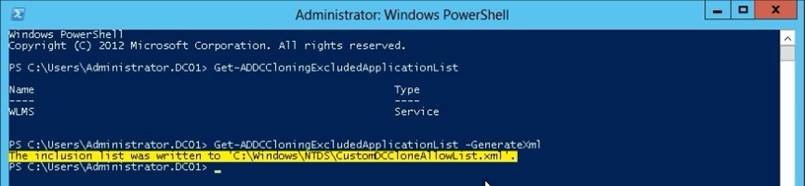
Get-ADDCCloningExcludedApplicationList -GenerateXml
The clone domain controller will be located in the same site as the source domain controller unless a different site is specified in the DCCloneConfig.xml file.
Note:
✑ The Get-ADDCCloningExcludedApplicationListcmdlet searches the local domain controller for programs and services in the installed programs database, the services control manager that are not specified in the default and user defined inclusion list. The applications in the resulting list can be added to the user defined exclusion list if they are determined to support cloning. If the applications are not cloneable, they should be removed from the source domain controller before the clone media is created. Any application that appears in cmdlet output and is not included in the user defined inclusion list will force cloning to fail.
✑ The Get-ADDCCloningExcludedApplicationListcmdlet needs to be run before the New- ADDCCloneConfigFilecmdlet is used because if the New- ADDCCloneConfigFilecmdlet detects an excluded application, it will not create a DCCloneConfig.xml file.
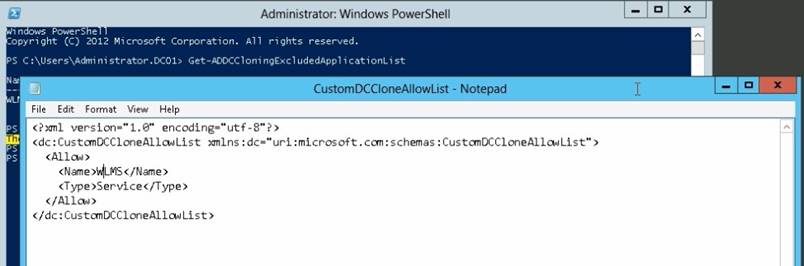
✑ DCCloneConfig.xml is an XML configuration file that contains all of the settings the cloned DC will take when it boots. This includes network settings, DNS, WINS, AD site name, new DC name and more. This file can be generated in a few different ways.
The New-ADDCCloneConfigcmdlet in PowerShell By hand with an XML editor
By editing an existing config file, again with an XML editor (Notepad is not an XML editor.)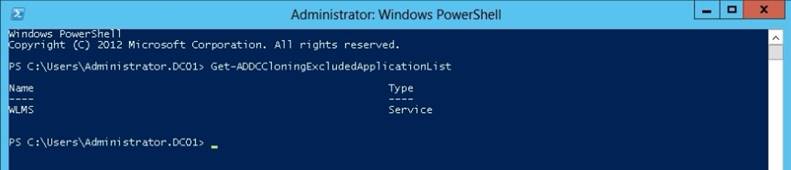
You can populate the XML file. . . . . doesn't need to be empty. . . . .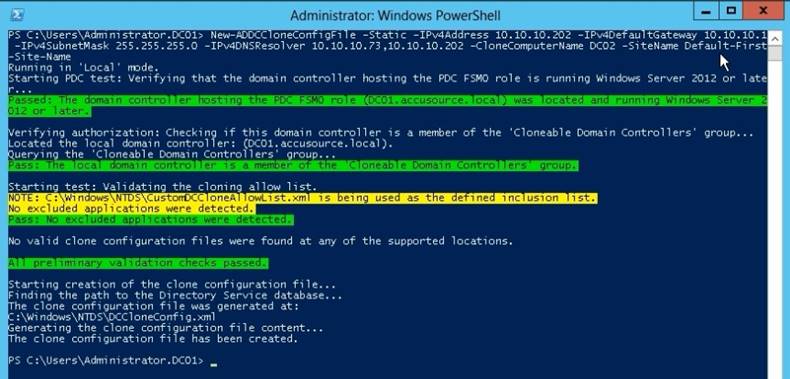
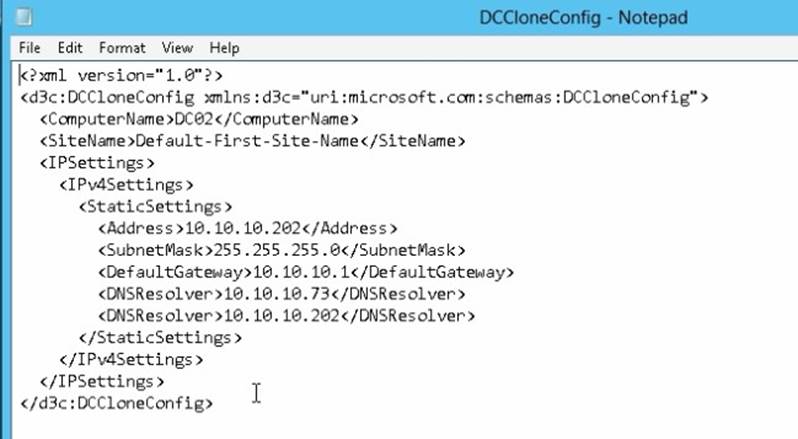
References:
http: //technet. microsoft. com/en-us/library/hh831734. aspx
http: //blogs. dirteam. com/blogs/sanderberkouwer/archive/2012/09/10/new-features-in- active-directory-domain-services-in-windows-server-2012-part-13-domain-controller- cloning. aspx
NEW QUESTION 17
HOTSPOT
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Remote Access server role installed.
You need to configure the ports on Server1 to ensure that client computers can establish VPN connections to Server1. The solution must NOT require the use of certificates or pre- shared keys.
What should you modify?
To answer, select the appropriate object in the answer area.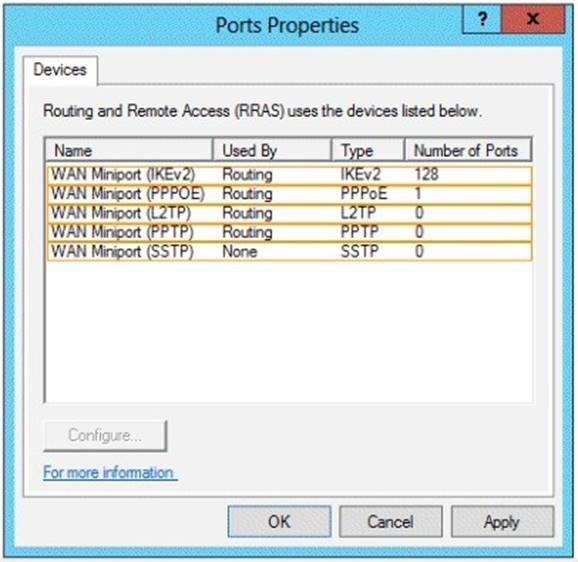
Answer:
Explanation: The four types of tunneling protocols used with a VPN/RAS server running on Windows Server 2012 include:
Point-to-Point Tunneling Protocol (PPTP): A VPN protocol based on the legacy Point-to- Point protocol used with modems. The PPTP specification does not describeencryption or authentication features and relies on the Point-to-Point Protocol being tunneled to implement security functionality.
Layer 2 Tunneling Protocol (L2TP): Used with IPsec to provide security. L2TP supports either computer certificates or a preshared key as the authentication method for IPsec. IKEv2: IKE is short for Internet Key Exchange, which is a tunneling protocol that uses IPsec Tunnel Mode protocol. The message is encrypted with one of the following protocols by using encryption keys that are generated from the IKEv2 negotiation process.
Secure Socket Tunneling Protocol (SSTP): Introduced with Windows Server 2008, which uses the HTTPS protocol over TCP port 443 to pass traffic through firewalls
References:
http: //en. wikipedia. org/wiki/Point-to-Point_Tunneling_Protocol
NEW QUESTION 18
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. All domain controllers run Windows Server 2012 R2.
The domain contains two domain controllers. The domain controllers are configured as shown in the following table.
Active Directory Recycle Bin is enabled.
You discover that a support technician accidentally removed 100 users from an Active Directory group named Group1 an hour ago.
You need to restore the membership of Group1. What should you do?
- A. Modify the isRecycledattribute of Group1.
- B. Perform tombstone reanimation.
- C. Perform a non-authoritative restore.
- D. Perform an authoritative restore.
Answer: D
NEW QUESTION 19
Your network contains an Active Directory domain named contoso.com. The domain contains a read-only domain controller (RODC) named RODC1.
You create a global group named RODC_Admins.
You need to provide the members of RODC_Admins with the ability to manage the hardware and the software on R0DC1. The solution must not provide RODC_Admins with the ability to manage Active Directory objects.
What should you do?
- A. From Active Directory Site and Services, configure the Security settings of the RODC1 server object.
- B. From Windows PowerShell, run the Set-ADAccountControlcmdlet.
- C. From a command prompt, run the dsmgmt local roles command.
- D. From Active Directory Users and Computers, configure the Member Of settings of the RODC1 account.
Answer: C
Explanation: RODC: using the dsmgmt.exe utility to manage local administrators
One of the benefits of RODC is that you can add local administrators who do not have full access to the domain administration. This gives them the ability to manage the server but not add or change active directory objects unless those roles are delegated. Adding this type of user is done using the dsmdmt.exe utility at the command prompt.
NEW QUESTION 20
Your network contains an Active Directory domain named contoso.com.
All user accounts reside in an organizational unit (OU) named OU1. All of the users in the marketing department are members of a group named Marketing. All of the users in the human resources department are members of a group named HR.
You create a Group Policy object (GPO) named GPO1. You link GPO1 to OU1. You configure the Group Policy preferences of GPO1 to add two shortcuts named Link1 and Link2 to the desktop of each user.
You need to ensure that Link1 only appears on the desktop of the users in Marketing and that Link2 only appears on the desktop of the users in HR.
What should you configure?
- A. Security Filtering
- B. WMI Filtering
- C. Group Policy Inheritance
- D. Item-level targeting
Answer: D
Explanation: You can use item-level targeting to change the scope of individual preference items, so they apply only to selected users or computers. Within a single Group Policy object (GPO), you can include multiple preference items, each customized for selected users or computers and each targeted to apply settings only to the relevant users or computers.
Reference: http://technet.microsoft.com/en-us/library/cc733022.aspx
100% Valid and Newest Version 70-411 Questions & Answers shared by DumpSolutions, Get Full Dumps HERE: https://www.dumpsolutions.com/70-411-dumps/ (New 294 Q&As)
