Exam Code: CAS-003 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: CompTIA Advanced Security Practitioner (CASP)
Certification Provider: CompTIA
Free Today! Guaranteed Training- Pass CAS-003 Exam.
CompTIA CAS-003 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
Which of the following represents important technical controls for securing a SAN storage infrastructure? (Select TWO).
- A. Synchronous copy of data
- B. RAID configuration
- C. Data de-duplication
- D. Storage pool space allocation
- E. Port scanning
- F. LUN masking/mapping
- G. Port mapping
Answer: FG
Explanation:
A logical unit number (LUN) is a unique identifier that designates individual hard disk devices or
grouped devices for address by a protocol associated with a SCSI, iSCSI, Fibre Channel (FC) or similar interface. LUNs are central to the management of block storage arrays shared over a storage area network (SAN).
LUN masking subdivides access to a given port. Then, even if several LUNs are accessed through the same port, the server masks can be set to limit each server's access to the appropriate LUNs. LUN masking is typically conducted at the host bus adapter (HBA) or switch level.
Port mapping is used in ‘Zoning’. In storage networking, Fibre Channel zoning is the partitioning of a Fibre Channel fabric into smaller subsets to restrict interference, add security, and to simplify management. While a SAN makes available several devices and/or ports to a single device, each system connected to the SAN should only be allowed access to a controlled subset of these devices/ports.
Zoning can be applied to either the switch port a device is connected to OR the WWN World Wide Name on the host being connected. As port based zoning restricts traffic flow based on the specific switch port a device is connected to, if the device is moved, it will lose access. Furthermore, if a different device is connected to the port in question, it will gain access to any resources the previous host had access to.
Incorrect Answers:
A: Synchronous copy of data is used to copy data. It is not a technical control for securing a SAN storage infrastructure.
B: RAID configuration is the configuration of the disks in the SAN. A RAID is an array of disks that provides a logical pool of storage by combining the storage capacity of the disks. RAID provides hardware redundancy in that the data will not be lost if an individual disk fails. RAID configuration is not a technical control for securing a SAN storage infrastructure.
C: Data de-duplication is the process of eliminating multiple copies of the same data to save storage space. It is not a technical control for securing a SAN storage infrastructure.
D: Storage pool space allocation is the process of allocating and making available portions of the storage pool to servers. It is not a technical control for securing a SAN storage infrastructure.
E: Port scanning is the process of probing a server or host for open ports. It is not a technical control for securing a SAN storage infrastructure.
References: http://searchvirtualstorage.techtarget.com/definition/LUN-masking https://en.wikipedia.org/wiki/Fibre_Channel_zoning
NEW QUESTION 2
The Chief Information Security Officer (CISO) is asking for ways to protect against zero-day explogts. The CISO is concerned that an unrecognized threat could compromise corporate data and result in regulatory fines as well as poor corporate publicity. The network is mostly flat, with split staff/guest wireless functionality. Which of the following equipment MUST be deployed to guard against unknown threats?
- A. Cloud-based antivirus solution, running as local admin, with push technology for definition updates.
- B. Implementation of an offsite data center hosting all company data, as well as deployment of VDI for all client computing needs.
- C. Host based heuristic IPS, segregated on a management VLAN, with direct control of the perimeter firewall ACLs.
- D. Behavior based IPS with a communication link to a cloud based vulnerability and threat fee
Answer: D
Explanation:
Good preventive security practices are a must. These include installing and keeping firewall policies carefully matched to business and application needs, keeping antivirus software updated, blocking
potentially harmful file attachments and keeping all systems patched against known vulnerabilities. Vulnerability scans are a good means of measuring the effectiveness of preventive procedures. Real- time protection: Deploy inline intrusion-prevention systems (IPS) that offer comprehensive protection. When considering an IPS, seek the following capabilities: network-level protection, application integrity checking, application protocol Request for Comment (RFC) validation, content validation and forensics capability. In this case it would be behavior-based IPS with a communication link to a cloud-based vulnerability and threat feed.
Incorrect Answers:
A: A cloud-based anti-virus solution will not protect against a zero-day explogt.
B: Due to the nature of zero-day explogts an off-site data center hosting solution for the company data is not the best protection against a zero-day explogt.
C: The best protection against zero-day explogts are behavior-based IPS and not hos-based heuristic IPS.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 194
https://en.wikipedia.orHYPERLINK "https://en.wikipedia.org/wiki/Zeroday_( computing)"g/wiki/Zero-day_%28computing%29
NEW QUESTION 3
A business is growing and starting to branch out into other locations. In anticipation of opening an office in a different country, the Chief Information Security Officer (CISO) and legal team agree they need to meet the following criteria regarding data to open the new office:
Store taxation-related documents for five years Store customer addresses in an encrypted format Destroy customer information after one year Keep data only in the customer’s home country
Which of the following should the CISO implement to BEST meet these requirements? (Choose three.)
- A. Capacity planning policy
- B. Data retention policy
- C. Data classification standard
- D. Legal compliance policy
- E. Data sovereignty policy
- F. Backup policy
- G. Acceptable use policy
- H. Encryption standard
Answer: BCH
NEW QUESTION 4
A multi-national company has a highly mobile workforce and minimal IT infrastructure. The company utilizes a BYOD and social media policy to integrate presence technology into global collaboration tools by individuals and teams. As a result of the dispersed employees and frequent international travel, the company is concerned about the safety of employees and their families when moving in and out of certain countries. Which of the following could the company view as a downside of using presence technology?
- A. Insider threat
- B. Network reconnaissance
- C. Physical security
- D. Industrial espionage
Answer: C
Explanation:
If all company users worked in the same office with one corporate network and using company supplied laptops, then it is easy to implement all sorts of physical security controls. Examples of physical security include intrusion detection systems, fire protection systems, surveillance cameras or simply a lock on the office door.
However, in this question we have dispersed employees using their own devices and frequently traveling internationally. This makes it extremely difficult to implement any kind of physical security. Physical security is the protection of personnel, hardware, programs, networks, and data from physical circumstances and events that could cause serious losses or damage to an enterprise,
agency, or institution. This includes protection from fire, natural disasters, burglary, theft, vandalism, and terrorism.
Incorrect Answers:
A: An insider threat is a malicious hacker (also called a cracker or a black hat) who is an employee or officer of a business, institution, or agency. Dispersed employees using presence technology does not increase the risk of insider threat when compared to employees working together in an office.
B: The risk of network reconnaissance is reduced by having dispersed employees using presence technology. The risk of network reconnaissance would be higher with employees working together in a single location such as an office.
D: Industrial espionage is a threat to any business whose livelihood depends on information. However, this threat is not increased by having dispersed employees using presence technology. The risk would be the same with dispersed employees using presence technology or employees working together in a single location such as an office.
References: http://searchsecurity.techtarget.com/deHYPERLINK
"http://searchsecurity.techtarget.com/definition/physical-security"finition/physical-security
NEW QUESTION 5
Management is reviewing the results of a recent risk assessment of the organization’s policies and procedures. During the risk assessment it is determined that procedures associated with background checks have not been effectively implemented. In response to this risk, the organization elects to revise policies and procedures related to background checks and use a third-party to perform background checks on all new employees. Which of the following risk management strategies has the organization employed?
- A. Transfer
- B. Mitigate
- C. Accept
- D. Avoid
- E. Reject
Answer: B
NEW QUESTION 6
A security manager is looking into the following vendor proposal for a cloud-based SIEM solution. The intention is that the cost of the SIEM solution will be justified by having reduced the number of incidents and therefore saving on the amount spent investigating incidents.
Proposal:
External cloud-based software as a service subscription costing $5,000 per month. Expected to reduce the number of current incidents per annum by 50%.
The company currently has ten security incidents per annum at an average cost of $10,000 per incident. Which of the following is the ROI for this proposal after three years?
- A. -$30,000
- B. $120,000
- C. $150,000
- D. $180,000
Answer: A
Explanation:
Return on investment = Net profit / Investment where: Net profit = gross profit - expenses.
or
Return on investment = (gain from investment – cost of investment) / cost of investment Subscriptions = 5,000 x 12 = 60,000 per annum
10 incidents @ 10,000 = 100.000 per annum reduce by 50% = 50,000 per annum
Thus the rate of Return is -10,000 per annum and that makes for -$30,000 after three years. References:
http://www.finHYPERLINK "http://www.financeformulas.net/Return_on_Investment.html"anceformulas.net/Return_on_Invest ment.html
NEW QUESTION 7
The technology steering committee is struggling with increased requirements stemming from an increase in telecommuting. The organization has not addressed telecommuting in the past. The implementation of a new SSL-VPN and a VOIP phone solution enables personnel to work from remote locations with corporate assets. Which of the following steps must the committee take FIRST to outline senior management’s directives?
- A. Develop an information classification scheme that will properly secure data on corporate systems.
- B. Implement database views and constrained interfaces so remote users will be unable to access PII from personal equipment.
- C. Publish a policy that addresses the security requirements for working remotely with company equipment.
- D. Work with mid-level managers to identify and document the proper procedures for telecommuting.
Answer: C
Explanation:
The question states that “the organization has not addressed telecommuting in the past”. It is therefore unlikely that a company policy exists for telecommuting workers.
There are many types of company policies including Working time, Equality and diversity, Change management, Employment policies, Security policies and Data Protection policies.
In this question, a new method of working has been employed: remote working or telecommuting. Policies should be created to establish company security requirements (and any other requirements) for users working remotely.
Incorrect Answers:
A: The data should already be secure on the corporate systems. If an information classification scheme is used as part of the security, it should already have been created. Remote working does not add the requirement for an information classification scheme.
B: The personnel work from remote locations with corporate assets; their personal computers are not used. Therefore, we do not require database views and constrained interfaces so remote users will be unable to access PII from personal equipment.
D: You should identify and document the proper procedures for telecommuting. However, the security requirements for working remotely with company equipment should be addressed first. Furthermore, you would not necessarily work with mid-level managers to identify and document the proper procedures for telecommuting if the company has a technology steering committee.
NEW QUESTION 8
Company ABC is hiring customer service representatives from Company XYZ. The representatives reside at Company XYZ’s headquarters. Which of the following BEST prevents Company XYZ representatives from gaining access to unauthorized Company ABC systems?
- A. Require each Company XYZ employee to use an IPSec connection to the required systems
- B. Require Company XYZ employees to establish an encrypted VDI session to the required systems
- C. Require Company ABC employees to use two-factor authentication on the required systems
- D. Require a site-to-site VPN for intercompany communications
Answer: B
Explanation:
VDI stands for Virtual Desktop Infrastructure. Virtual desktop infrastructure is the practice of hosting a desktop operating system within a virtual machine (VM) running on a centralized server.
Company ABC can configure virtual desktops with the required restrictions and required access to systems that the users in company XYZ require. The users in company XYZ can then log in to the virtual desktops over a secure encrypted connection and then access authorized systems only. Incorrect Answers:
A: Requiring IPSec connections to the required systems would secure the connections to the required systems. However, it does not prevent access to unauthorized systems.
C: The question states that the representatives reside at Company XYZ’s headquarters. Therefore, they will be access Company ABC’s systems remotely. Two factor authentication requires that the user be present at the location of the system to present a smart card or for biometric authentication; two factor authentication cannot be performed remotely.
D: A site-to-site VPN will just create a secure connection between the two sites. It does not restrict access to unauthorized systems.
References:
http://searchvHYPERLINK "http://searchvirtualdesktop.techtarget.com/definition/virtualdesktop" irtualdesktop.techtarget.com/definition/virtual-desktop
NEW QUESTION 9
A security administrator wants to calculate the ROI of a security design which includes the purchase of new equipment. The equipment costs $50,000 and it will take 50 hours to install and configure the equipment. The administrator plans to hire a contractor at a rate of $100/hour to do the installation. Given that the new design and equipment will allow the company to increase revenue and make an additional $100,000 on the first year, which of the following is the ROI expressed as a percentage for the first year?
- A. -45 percent
- B. 5.5 percent
- C. 45 percent
- D. 82 percent
Answer: D
Explanation:
Return on investment = Net profit / Investment where: Net profit = gross profit – expenses
investment = stock + market outstanding[when defined as?] + claims or
Return on investment = (gain from investment – cost of investment) / cost of investment Thus (100 000 – 55 000)/50 000 = 0,82 = 82 %
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 337 http://www.financeformulas.net/Return_on_Investment.html
NEW QUESTION 10
A security consultant is attempting to discover if the company is utilizing databases on client machines to store the customer data.
The consultant reviews the following information: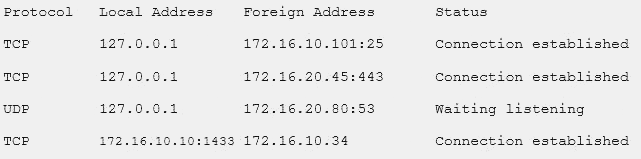
Which of the following commands would have provided this output?
- A. arp -s
- B. netstat -a
- C. ifconfig -arp
- D. sqlmap -w
Answer: B
NEW QUESTION 11
An administrator believes that the web servers are being flooded with excessive traffic from time to time. The administrator suspects that these traffic floods correspond to when a competitor makes major announcements. Which of the following should the administrator do to prove this theory?
- A. Implement data analytics to try and correlate the occurrence times.
- B. Implement a honey pot to capture traffic during the next attack.
- C. Configure the servers for high availability to handle the additional bandwidth.
- D. Log all traffic coming from the competitor's public IP addresse
Answer: A
Explanation:
There is a time aspect to the traffic flood and if you correlate the data analytics with the times that the incidents happened, you will be able to prove the theory.
Incorrect Answers:
B: A honey pot is designed to attract traffic and this will not prove the theory.
C: Configuring any of your servers for high availability will only accommodate the competitor and not prove your theory.
D: Logging all incoming traffic will not prove the theory as you want to check whether the incidents occur when the competitor makes major announcement a not all of the incoming traffic, even it if is from the competitor.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 114-115
NEW QUESTION 12
A technician receives the following security alert from the firewall's automated system: Match_Time: 10/10/16 16:20:43
Serial: 002301028176
Device_name: COMPSEC1 Type: CORRELATION
Scrusex: domain\samjones Scr: 10.50.50.150
Object_name: beacon detection Object_id: 6005
Category: compromised-host Severity: medium
Evidence: host repeatedly visited a dynamic DNS domain (17 time) After reviewing the alert, which of the following is the BEST analysis?
- A. the alert is a false positive because DNS is a normal network function.
- B. this alert indicates a user was attempting to bypass security measures using dynamic DNS.
- C. this alert was generated by the SIEM because the user attempted too many invalid login attempts.
- D. this alert indicates an endpoint may be infected and is potentially contacting a suspect hos
Answer: B
NEW QUESTION 13
A hospital uses a legacy electronic medical record system that requires multicast for traffic between the application servers and databases on virtual hosts that support segments of the application. Following a switch upgrade, the electronic medical record is unavailable despite physical connectivity between the hypervisor and the storage being in place. The network team must enable multicast traffic to restore access to the electronic medical record. The ISM states that the network team must reduce the footprint of multicast traffic on the network.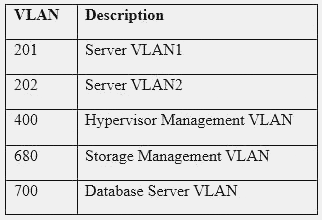
Using the above information, on which VLANs should multicast be enabled?
- A. VLAN201, VLAN202, VLAN400
- B. VLAN201, VLAN202, VLAN700
- C. VLAN201, VLAN202, VLAN400, VLAN680, VLAN700
- D. VLAN400, VLAN680, VLAN700
Answer: D
NEW QUESTION 14
A security engineer is a new member to a configuration board at the request of management. The company has two new major IT projects starting this year and wants to plan security into the application deployment. The board is primarily concerned with the applications’ compliance with federal assessment and authorization standards. The security engineer asks for a timeline to determine when a security assessment of both applications should occur and does not attend subsequent configuration board meetings. If the security engineer is only going to perform a security assessment, which of the following steps in system authorization has the security engineer omitted?
- A. Establish the security control baseline
- B. Build the application according to software development security standards
- C. Review the results of user acceptance testing
- D. Consult with the stakeholders to determine which standards can be omitted
Answer: A
Explanation:
A security baseline is the minimum level of security that a system, network, or device must adhere to. It is the initial point of reference for security and the document against which assessments would be done.
Incorrect Answers:
B: Building the application with secure coding is the programmers’ duty. C: User acceptance testing is part of the development process
D: Standards are not security concerns. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 272-273
NEW QUESTION 15
An organization has established the following controls matrix: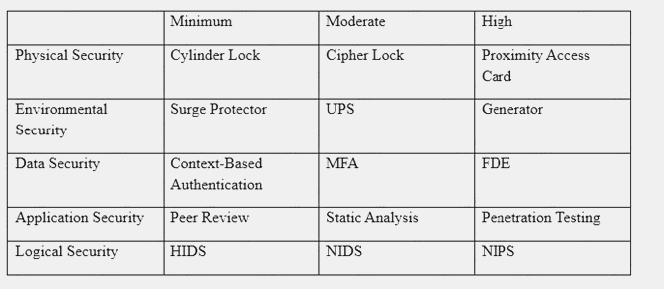
The following control sets have been defined by the organization and are applied in aggregate fashion:
Systems containing PII are protected with the minimum control set. Systems containing medical data are protected at the moderate level. Systems containing cardholder data are protected at the high level.
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
- A. Proximity card access to the server room, context-based authentication, UPS, and full-disk encryption for the database server.
- B. Cipher lock on the server room door, FDE, surge protector, and static analysis of all application code.
- C. Peer review of all application changes, static analysis of application code, UPS, and penetration testing of the complete system.
- D. Intrusion detection capabilities, network-based IPS, generator, and context-based authenticatio
Answer: D
NEW QUESTION 16
A company decides to purchase commercially available software packages. This can introduce new security risks to the network. Which of the following is the BEST description of why this is true?
- A. Commercially available software packages are typically well known and widely available.Information concerning vulnerabilities and viable attack patterns are never revealed by the developer to avoid lawsuits.
- B. Commercially available software packages are often widely availabl
- C. Information concerning vulnerabilities is often kept internal to the company that developed the software.
- D. Commercially available software packages are not widespread and are only available in limited area
- E. Information concerning vulnerabilities is often ignored by business managers.
- F. Commercially available software packages are well known and widely availabl
- G. Information concerning vulnerabilities and viable attack patterns are always shared within the IT community.
Answer: B
Explanation:
Commercially available software packages are often widely available. Huge companies like Microsoft develop software packages that are widely available and in use on most computers. Most companies that develop commercial software make their software available through many commercial outlets (computer stores, online stores etc).
Information concerning vulnerabilities is often kept internal to the company that developed the software. The large companies that develop commercial software packages are accountable for the software. Information concerning vulnerabilities being made available could have a huge financial cost to the company in terms of loss of reputation and lost revenues. Information concerning vulnerabilities is often kept internal to the company at least until a patch is available to fix the vulnerability.
Incorrect Answers:
A: It is true that commercially available software packages are typically well known and widely available. However, it is not true that information concerning vulnerabilities and viable attack patterns are never revealed by the developer to avoid lawsuits. Information concerning vulnerabilities is often kept quiet at first but the information is usually made available when a patch is released to fix the vulnerability.
C: It is not true that commercially available software packages are not widespread and are only available in limited areas.
D: It is true that commercially available software packages are typically well known and widely available. However, it is not true that information concerning vulnerabilities and viable attack patterns are always shared within the IT community. This information is often kept internal to the company that developed the software until a patch is available.
NEW QUESTION 17
A web developer has implemented HTML5 optimizations into a legacy web application. One of the modifications the web developer made was the following client side optimization: localStorage.setItem(“session-cookie”, document.cookie);
Which of the following should the security engineer recommend?
- A. SessionStorage should be used so authorized cookies expire after the session ends
- B. Cookies should be marked as “secure” and “HttpOnly”
- C. Cookies should be scoped to a relevant domain/path
- D. Client-side cookies should be replaced by server-side mechanisms
Answer: C
NEW QUESTION 18
An organization is currently working with a client to migrate data between a legacy ERP system and a cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is
performing data deduplication and sanitization of client data to ensure compliance with regulatory requirements. Which of the following is the MOST likely reason for the need to sanitize the client data?
- A. Data aggregation
- B. Data sovereignty
- C. Data isolation
- D. Data volume
- E. Data analytics
Answer: A
NEW QUESTION 19
......
100% Valid and Newest Version CAS-003 Questions & Answers shared by Allfreedumps.com, Get Full Dumps HERE: https://www.allfreedumps.com/CAS-003-dumps.html (New 555 Q&As)
