Cause all that matters here is passing the CompTIA CV0-002 exam. Cause all that you need is a high score of CV0-002 CompTIA Cloud+ Exam exam. The only one thing you need to do is downloading Pass4sure CV0-002 exam study guides now. We will not let you down with our money-back guarantee.
Online CompTIA CV0-002 free dumps demo Below:
NEW QUESTION 1
A company is expanding its cloud hosting services to include storage. Prior to upgrading existing customers with the new service, the testing department needs to validate that users can access the new service without seeing other customer data or company sensitive data also hosted in the cloud environment. Which of the following should be conducted prior to deployment of the new service?
- A. Bandwidth test
- B. Load balancing
- C. Security test
- D. Storage test
Answer: C
NEW QUESTION 2
A university is running a DNA decoding project that will take seven years if it runs on its current
internal mainframe. The university negotiated a deal with a large cloud provider, which will donate its cloud resource to process the DNA decoding during the low peak time throughout the world. Which of the following is the MOST important resource the university should ask the cloud provider to donate?
- A. A large storage for the DNA decoding results
- B. A larger pipe to transfer the results
- C. A closer datacenter to the university
- D. Any available compute resource
Answer: C
NEW QUESTION 3
An administrator has been promoted to architect when trying to access one of the servers, the
architect receives the error: “Authentication failure: Account is not allowed”. Which of the following explains why access was denied?
- A. Role-based ACL are enabled
- B. Multifactor authentication is partially working
- C. Federated information is not completely populated
- D. Discretionary ACL are enabled
Answer: D
NEW QUESTION 4
Which of the following would be appropriate when considering inbound access security for a web-
based SaaS solution?
- A. Antivirus/anti-malware
- B. IPSec
- C. Firewall
- D. Obfuscation
Answer: B
NEW QUESTION 5
A cloud provider is increasingly discovering hard-to-find issues within the growing infrastructure. The
provider has all the basic necessary tools implemented to collect and store data regarding the environment. To allow the cloud provider to focus on relevant events, which of the following is the MOST appropriate technique to build intelligence?
- A. Event correlation
- B. Event collection
- C. Event alerts
- D. Event-based workflows
Answer: B
NEW QUESTION 6
An administrator needs to verify what ports are listening on an operating system. Which of the
following tools can be used to accomplish this task?
- A. telnet
- B. netstat
- C. packet sniffer
- D. ifconfig
Answer: B
NEW QUESTION 7
An administrator for a non-profit organization has been tasked with creating a flexible cloud solution.
Which of the following would allow the programmer to customize this implementation?
- A. Type II virtual infrastructure
- B. Closed Source Hypervisors
- C. Open Source Hypervisors
- D. Type I virtual infrastructure
Answer: C
NEW QUESTION 8
An administrator is unable to connect to servers in the DMZ. Which of the following commands should the administrator run to determine where the connection failure occurs?
- A. nslookup
- B. traceroute
- C. telnet
- D. netstat
Answer: B
NEW QUESTION 9
Which of the following is the BEST way to achieve network throughput on any host with existing
NICs?
- A. 802.3ad
- B. 802.3x
- C. 802.11n
- D. 802.11i
Answer: C
NEW QUESTION 10
A new private cloud platform is being deployed by an engineer. SLA requirements state that any
clusters should have a baseline redundancy sufficient to handle the failure of at least two hosts. The engineer records the following metrics after the deployment: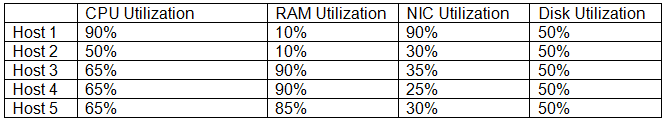
Which of the following metrics is MOST likely to represent a violation of SLA?
- A. RAM utilization
- B. NIC utilization
- C. CPU utilization
- D. Disk utilization
Answer: D
NEW QUESTION 11
Which of the following ensures that there is enough space for vendors to install their programs and
run the software they will be managing for various SaaS products?
- A. Network isolation
- B. Laws and regulations
- C. Multi-tenancy
- D. Data segregation
Answer: D
NEW QUESTION 12
An e-commerce business recently experienced a two-hour outage from its hosted web service
provider. According to the SLA, the business needs to determine how much data can be restored. On which of the following service-level components should the business focus?
- A. MTTR
- B. RPO
- C. MTBF
- D. RTO
Answer: C
NEW QUESTION 13
Which of the following can be used to physically restrict employees from accessing a datacenter?
- A. Access badge
- B. Password
- C. Mantrap
- D. PIN
Answer: A
NEW QUESTION 14
A cloud administrator updates the syslog forwarder configuration on a local server in production to
use a different port. The development team is no longer receiving the audit logs from that server. However, the security team can retrieve and search the logs for the same server. Which of the following is MOST likely the issue?
- A. The development team is not looking at the correct server when querying for the logs.
- B. The security team has greater permissions than the development team.
- C. The audit logging service has been disabled on the server.
- D. The development team’s syslog server is configured to listen on the wrong port.
Answer: B
NEW QUESTION 15
Which of the following is a best practice used in relation to MTBF?
- A. Determine backup schedule based on uptime requirements
- B. Proactively replace components before they fail
- C. Determine downtime to perform a system recovery
- D. Reactively replace components after failure
Answer: B
NEW QUESTION 16
The helpdesk starts receiving calls from a number of users that are suddenly having issues accessing one of the project management shared drives. When Joe, an administrator, logs onto the guest hosting the drive via the console he is able to get to the information. Which of the following failures could have caused this issue?
- A. NIC failure
- B. Disk failure
- C. Memory failure
- D. CPU failure
Answer: A
NEW QUESTION 17
Which of the following server types would be an ideal candidate for virtualization? (Select two.)
- A. Hypervisor
- B. Terminal server
- C. Mail server
- D. Enterprise database server
- E. Domain controller
Answer: CD
NEW QUESTION 18
The Chief Information Officer (CIO) has established the requirement to limit data loss to within two
hours of a disaster. Which of the following terms describes this requirement?
- A. RTO
- B. RPO
- C. MTTR
- D. MTBF
Answer: B
NEW QUESTION 19
An administrator is configuring a website in the cloud. Which of the following secure network
protocols should the administrator configure?
- A. HTTP
- B. IPSEC
- C. SSL
- D. SSH
Answer: C
NEW QUESTION 20
An administrator is attempting to troubleshoot an issue between a web server in the DMZ and an internal workstation by reviewing packet captures. Upon inspection, the payloads of the packets are unreadable. Which of the following could be the cause of this issue?
- A. The administrator has yet to authenticate to the network
- B. The sniffer is located on an incorrect subnet
- C. A vulnerability scanner has interfered with the packet capture
- D. End-to-end encryption is applied on the network
Answer: A
NEW QUESTION 21
Which of the following authentication types is being required when a user must swipe a key card and
then enter a password before being allowed access to the server room?
- A. Multi-factor authentication
- B. Single sign-on
- C. Biometric authentication
- D. Single-factor authentication
Answer: A
NEW QUESTION 22
A cloud implementation engineer successfully created a new VM. However, the engineer notices the new VM is not accessible from another network. A ping test works from another VM on the same subnet. Which of the following is the MOST likely problem?
- A. Incorrect subnet
- B. Incorrect host IP address
- C. Incorrect VLAN
- D. Incorrect gateway
Answer: A
NEW QUESTION 23
......
P.S. Easily pass CV0-002 Exam with 317 Q&As Certshared Dumps & pdf Version, Welcome to Download the Newest Certshared CV0-002 Dumps: https://www.certshared.com/exam/CV0-002/ (317 New Questions)
