Exam Code: CV0-002 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: CompTIA Cloud+ Exam
Certification Provider: CompTIA
Free Today! Guaranteed Training- Pass CV0-002 Exam.
CompTIA CV0-002 Free Dumps Questions Online, Read and Test Now.
NEW QUESTION 1
A virtual machine snapshot is:
- A. a backup copy of the virtual machine.
- B. a revertible point in time of the virtual machine.
- C. an exact copy of the virtual machine.
- D. an image of the virtual machine.
Answer: B
NEW QUESTION 2
An administrator, who operates a public cloud, has been tasked with implementing a secondary
datacenter for failover purposes. Immediate replication has too much of an impact on the WAN link during production hours. Which of the following is the BEST option?
- A. Asynchronous replication
- B. Storage deduplication
- C. Cold site failover with offsite archiving
- D. Site mirroring
Answer: A
NEW QUESTION 3
Which of the following cloud services would MOST likely be selected by a software development
company that needs a cloud in which to develop software and does not have infrastructure requirements?
- A. PaaS
- B. SaaS
- C. IaaS
- D. XaaS
Answer: A
NEW QUESTION 4
A host with 30 VMs has 64GB of RAM, four quad-core CPUs, four 1-gigabit NICs and is connected to a NAS that provides NFS volumes. The hosted VMs are reporting slow performance. From the information given, which of the following is the MOST likely cause of the slow performance?
- A. Insufficient NAS capacity
- B. The server is using 110V instead of 220V
- C. One hard drive has failed in the RAID 5
- D. Insufficient network capacity
Answer: D
NEW QUESTION 5
A company has decided to scale its e-commerce application from its corporate datacenter to a
commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday. The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations. The remote computing environment is connected to the on- premises datacenter via a site-to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully. Review the network architecture and supporting documents and fulfill these requirements:
1. Analyze the configuration of the following components:
DNS, Firewall1, Firewall2, Router1, Rouler2, VPN and Orchestrator Server.
2. Identify the problematic device(s).
Identify the correct options to provide adequate configuration for hybrid cloud architecture.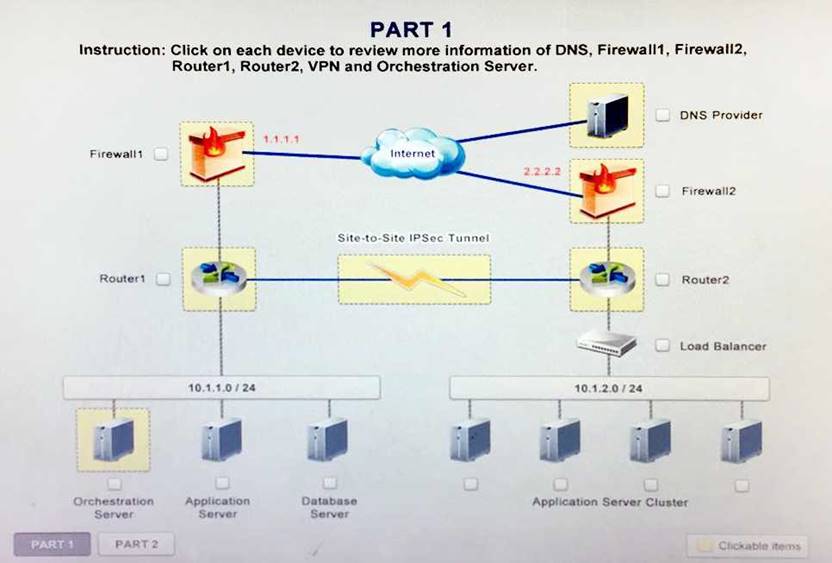
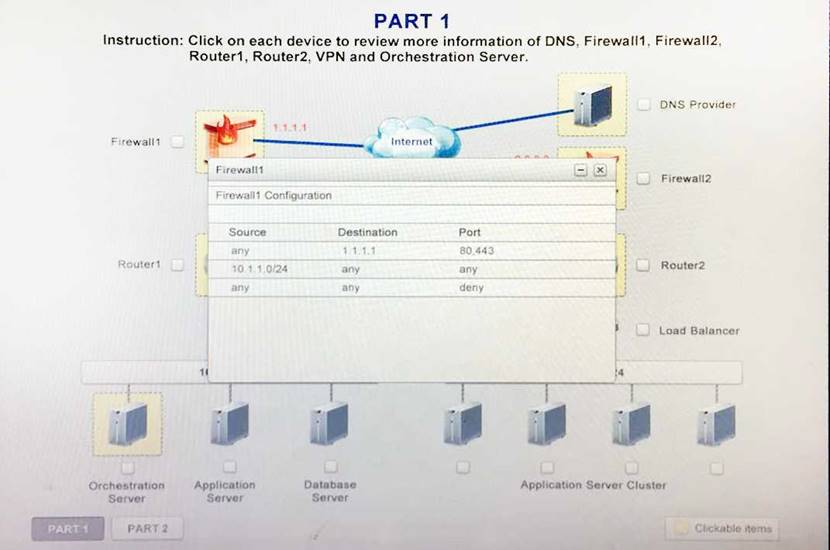
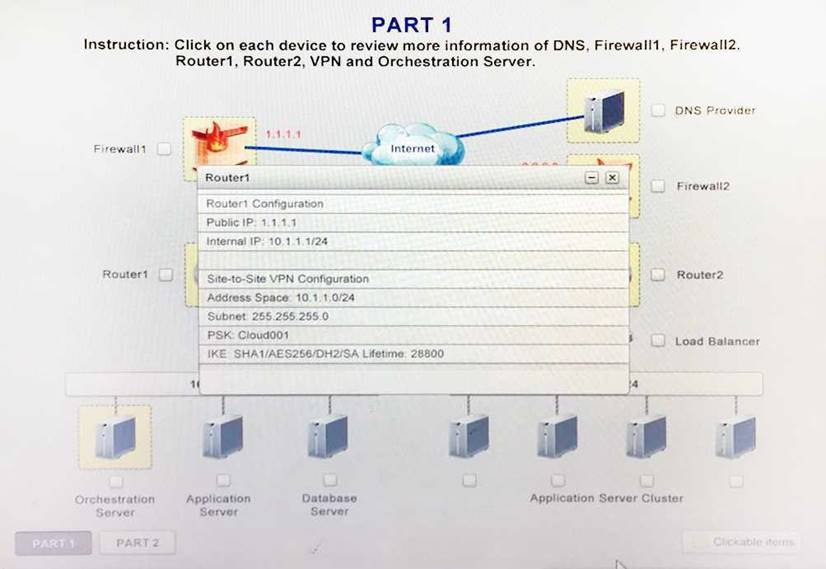
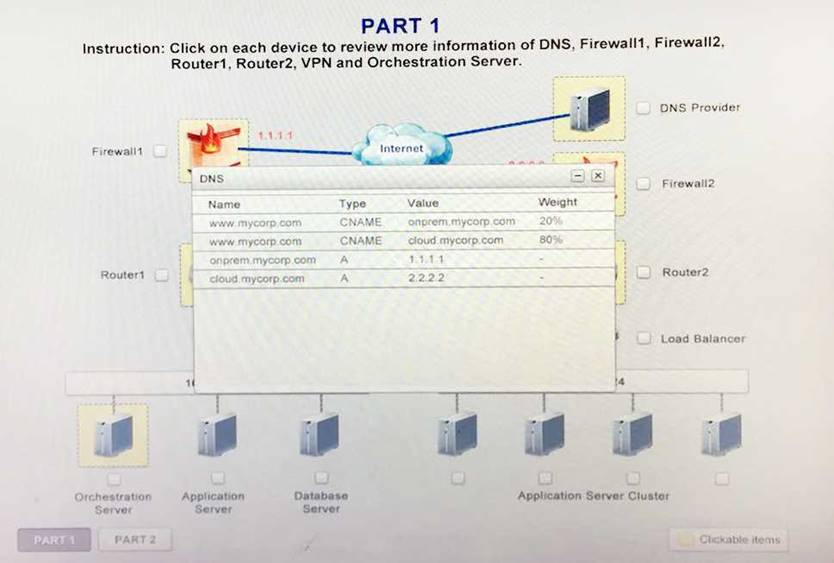
Instruction: Only select a maximum of TWO options from the multiple choice question
- A. Deploy a Replica of the Database Server in the Cloud Provider
- B. Update the PSK (Pre-shared key in Router2)
- C. Update the A record on the DNS from 2.2.2.2 to 1.1.1.1
- D. Promote deny All to allow All in Firewall1 and Firewall2
- E. Change the Address Space on Router2
- F. Change internal IP Address of Router1
- G. Reverse the Weight property in the two CNAME records on the DNS
- H. Add the Application Server at on-premises to the Load Balancer
Answer: AH
NEW QUESTION 6
An administrator has created a new virtual server according to specifications and verified that TCP/IP
settings are correct. When the VM is powered on, however, an error message indicates that a network card MAC address conflict exists. Which of the following would resolve this issue?
- A. Remove the virtual NIC and configure another one.
- B. Add an additional NIC with a loopback interface.
- C. Ping the IP address to determine the location of the conflict.
- D. Change the MAC to ff:ff:ff:ff:ff:ff and obtain a new address.
Answer: A
NEW QUESTION 7
A cloud engineer notices on a dashboard that the host is close to reaching maximum capacity for the CPU and memory in the cloud environment, which could cause performance issues. The cloud environment has 100 servers, with 25% of the servers consuming their compute only during peak business hours, 25% consuming half of the allocated resources, and the remaining 50% using the compute during off hours. Which of the following should the engineer perform to optimize the efficiency of the compute usage in the cloud?
- A. Add additional CPUs and RAM to the host that is serving the cloud.
- B. Adjust the cloud workload by migrating resource-intensive applications to different hosts.
- C. Add additional hosts to the environment using the cloud management tool.
- D. Enable automatic scaling in the cloud management tool.
Answer: B
NEW QUESTION 8
An administrator has recently moved all VoIP to a CaaS offering. In order to ensure that VoIP traffic
remains separate from the rest of the data traffic, which of the following MUST be done?
- A. All VoIP traffic needs to be VLAN tagged
- B. The CaaS CSP needs to create a new subnet
- C. The CaaS CSP needs to create a private VPN
- D. All VoIP traffic needs to have QoS
Answer: A
NEW QUESTION 9
Which of the following terms describes a system where multiple storage controllers allow access to data in a cloud environment where it appears as a single storage system to the user?
- A. Flexible volume
- B. Paired storage
- C. Virtualized storage
- D. Shared volume
Answer: D
NEW QUESTION 10
Which of the following is a hardening technique that an administrator would perform when creating a standard VM template that would be used for deploying servers in a production environment?
- A. Create a standard user account
- B. Disable unneeded services
- C. Establish a performance baseline
- D. Follow change management process
Answer: D
NEW QUESTION 11
The system administrator created a file sharing service to the cloud for easier access for those
working remotely. Which of the following tests should be performed to determine if services can be compromised?
- A. Test storage
- B. Test latency
- C. Vulnerability assessment
- D. Penetration testing
Answer: D
NEW QUESTION 12
A software development company is building cloud-ready applications and needs to determine the
best approach for releasing software. Which of the following approaches should be used?
- A. Perform QA, develop, test, and release to production
- B. Test, perform QA, develop, and release to production
- C. Develop, perform QA, test, and release to production
- D. Develop, test, perform QA, and release to production
Answer: D
NEW QUESTION 13
Fault tolerant design allows a host to overcome a single HBA failure through:
- A. clustering
- B. UTA pairing
- C. multipathing
- D. NIC teaming
Answer: A
Explanation:
Reference:
http://www.ques10.com/p/2619/write-short-note-on-failure-analysis/
NEW QUESTION 14
Which of the following tools would an administrator use when determining the hop count between a source and a destination?
- A. arp
- B. nbstat
- C. ipconfig
- D. tracert
Answer: D
NEW QUESTION 15
An administrator is responsible for managing a private cloud that has servers that require a significant amount of RAM, but does not have the resources to dedicate to the guests. Which of the following features should the administrator configure on the hypervisor?
- A. Resource pooled memory
- B. Memory reservation
- C. Dynamic memory
- D. Static memory
Answer: B
NEW QUESTION 16
A cloud administrator notices one of the servers is using the wrong set of NTP servers. The administrator needs to avoid the same issue in the future but needs to minimize administration resources. Which of the following tools should a cloud administrator deploy to meet this requirement?
- A. Patching tools
- B. Monitoring tools
- C. Configuration tools
- D. Deployment tools
Answer: D
NEW QUESTION 17
DRAG DROP
A hosted file share was infected with CryptoLocker and now root cause analysis needs to be performed. Place the tasks in the correct order according to the troubleshooting methodology.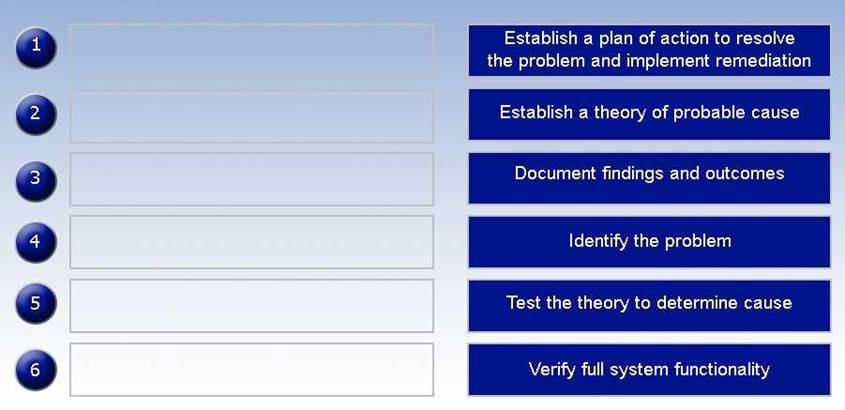
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 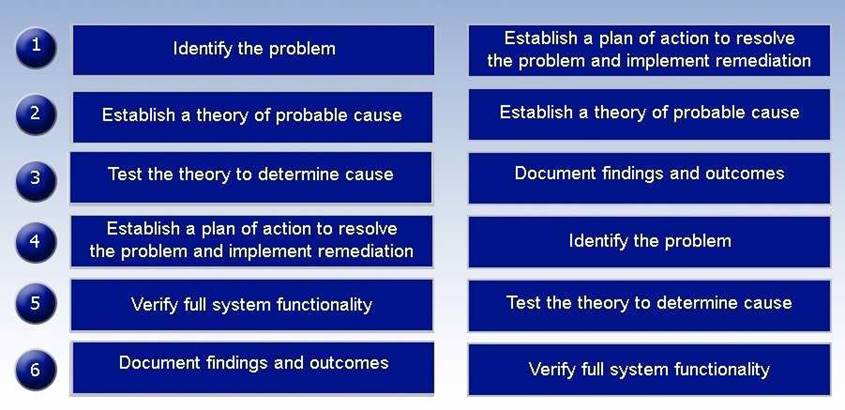
NEW QUESTION 18
Which of the following technologies allows for the secure exchange of encryption keys within an
internal network?
- A. AES
- B. RC4
- C. Diffie-Hellman
- D. 3DES
Answer: C
NEW QUESTION 19
Metadata is described as which of the following?
- A. A unique data field.
- B. A description of a data element.
- C. A file header.
- D. A large data object.
Answer: B
NEW QUESTION 20
A company is looking for a hardware feature with the least amount of downtime in terms of firmware
upgrades. Which of the following features BEST meet this requirement?
- A. In-service upgrades
- B. Rolling upgrades
- C. Failover upgrades
- D. User-mode upgrades
Answer: B
NEW QUESTION 21
A company hosts its server in a public IaaS cloud. The company’s management decides to migrate the servers to a different geographical region that is closer to the user base. A cloud administrator creates a new environment in that geographical region. Which of the following is the BEST way to migrate the VM from the original geographic region to the new region?
- A. 1. Create a full backup of the VM.2. Copy the backup files into the new region using FTP.3. Restore the VM from the backup files.
- B. 1. Create a VM image.2. Export the VM image to the new region using vendor’s tools.3. Deploy a new VM based on the created image.
- C. 1. Create a VM clone.2. Copy the clone into the new region using FTP.3. Apply the network and security groups from the new region to the cloned VM and start it.
- D. 1. Create a new VM in the new region.2. Restore a full-system backup from the original VM.3. Apply the network and security groups from the original region to the new VM.
Answer: D
NEW QUESTION 22
Implementing a process in a change management system takes place after:
- A. rigorous peer review.
- B. consultation with the vendor.
- C. initial test in a sandbox.
- D. approval by the CAB.
Answer: D
NEW QUESTION 23
......
100% Valid and Newest Version CV0-002 Questions & Answers shared by Downloadfreepdf.net, Get Full Dumps HERE: https://www.downloadfreepdf.net/CV0-002-pdf-download.html (New 317 Q&As)
