Passleader GCIA Questions are updated and all GCIA answers are verified by experts. Once you have completely prepared with our GCIA exam prep kits you will be ready for the real GCIA exam without a problem. We have Most up-to-date GIAC GCIA dumps study guide. PASSED GCIA First attempt! Here What I Did.
Online GCIA free questions and answers of New Version:
NEW QUESTION 1
Which of the following honeypots is a low-interaction honeypot and is used by companies or corporations for capturing limited information about malicious hackers?
- A. Production honeypot
- B. Research honeypot
- C. Honeynet
- D. Honeyfarm
Answer: A
NEW QUESTION 2
A firewall is a combination of hardware and software, used to provide security to a network. It is used to protect an internal network or intranet against unauthorized access from the Internet or other outside networks. It restricts inbound and outbound access and can analyze all traffic between an internal network and the Internet. Users can configure a firewall to pass or block packets from specific IP addresses and ports. Which of the following tools works as a firewall for the Linux 2.4 kernel?
- A. IPTables
- B. OpenSSH
- C. IPChains
- D. Stunnel
Answer: A
NEW QUESTION 3
Which of the following utilities produces the output displayed in the image below?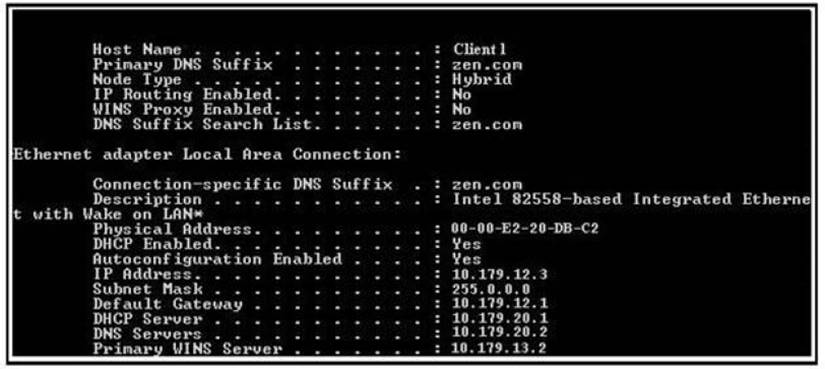
- A. IPCONFIG
- B. TRACERT
- C. PING
- D. PATHPING
Answer: A
NEW QUESTION 4
Which of the following ports can be used for IP spoofing?
- A. NNTP 119
- B. POP 110
- C. Rlogin 513
- D. Whois 43
Answer: C
NEW QUESTION 5
Which of the following is the process of categorizing attack alerts produced from IDS?
- A. Blocking
- B. Site policy implementation
- C. Intrusion classify
- D. Alarm filtering
Answer: D
NEW QUESTION 6
Which of the following statements is NOT true about FAT16 file system?
Each correct answer represents a complete solution. Choose all that apply.
- A. FAT16 file system supports Linux operating syste
- B. FAT16 file system supports file-level compressio
- C. FAT16 file system works well with large disks because the cluster size increases as the disk partition size increase
- D. FAT16 does not support file-level securit
Answer: BC
NEW QUESTION 7
Which of the following is the primary TCP/IP protocol used to transfer text and binary files over the Internet?
- A. PPTP
- B. SNMP
- C. FTP
- D. SMTP
Answer: C
NEW QUESTION 8
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple smallsized packets to the target computer. Hence, it becomes very difficult for an IDS to detect the attack signatures of such attacks. Which of the following tools can be used to perform session splicing attacks?
Each correct answer represents a complete solution. Choose all that apply.
- A. Nessus
- B. Y.A.
- C. Whisker
- D. Fragroute
Answer: AC
NEW QUESTION 9
Which of the following partitions contains the system files that are used to start the operating system?
- A. Boot partition
- B. System partition
- C. Secondary partition
- D. Primary partition
Answer: A
NEW QUESTION 10
Which of the following are the types of intrusion detection systems?
Each correct answer represents a complete solution. Choose all that apply.
- A. Server-based intrusion detection system (SIDS)
- B. Network intrusion detection system (NIDS)
- C. Client-based intrusion detection system (CIDS)
- D. Host-based intrusion detection system (HIDS)
Answer: BD
NEW QUESTION 11
Which of the following is computed from an arbitrary block of digital data for the purpose of detecting accidental errors?
- A. Hash filter
- B. Checksum
- C. Hash buster
- D. Firewall
Answer: B
NEW QUESTION 12
Which of the following commands prints out the headers of packets regarding the boolean expression?
- A. tcpdump
- B. vmstat
- C. iftop
- D. iostat
Answer: A
NEW QUESTION 13
Which of the following DoS attacks points the Central Processing Unit (CPU) to a non-existent memory location causing the running process to end abruptly?
- A. Buffer Overflow attack
- B. Teardrop attack
- C. Fraggle attack
- D. Snork attack
Answer: A
NEW QUESTION 14
Which of the following is a hardware/software platform that is designed to analyze, detect, and report on security related events. NIPS is designed to inspect traffic and based on its configuration or security policy, it can drop the malicious traffic?
- A. NIPS
- B. HIPS
- C. NIDS
- D. HIDS
Answer: A
NEW QUESTION 15
Which of the following terms is used to represent IPv6 addresses?
- A. Colon-dot
- B. Colon-hexadecimal
- C. Hexadecimal-dot notation
- D. Dot notation
Answer: B
NEW QUESTION 16
In which of the following IKE phases the IPsec endpoints establish parameters for a secure ISAKMP session?
- A. IKE Phase 2.5
- B. IKE Phase 2
- C. IKE Phase 1
- D. IKE Phase 1.5
Answer: C
NEW QUESTION 17
What is the maximum size of an IP datagram for Ethernet?
- A. 4500 bytes
- B. 1024 bytes
- C. 1200 bytes
- D. 1500 bytes
Answer: D
NEW QUESTION 18
Mark works as the Network Administrator of a Windows 2000 based network. The network has a DNS server installed. He experiences host name resolution problems on the network. In order to rectify the situation, he wants to troubleshoot DNS name resolution problems on the network.
Which of the following tools will he use to do this?
- A. NSLOOKUP
- B. IPCONFIG
- C. NBTSTAT
- D. NETSTAT
Answer: A
NEW QUESTION 19
You are using a Windows-based sniffer named ASniffer to record the data traffic of a network. You have extracted the following IP Header information of a randomly chosen packet from the sniffer's log:
45 00 00 28 00 00 40 00 29 06 43 CB D2 D3 82 5A 3B 5E AA 72
Which of the following TTL decimal values and protocols are being carried by the IP Header of this packet?
- A. 41, UDP
- B. 16, ICMP
- C. 41, TCP
- D. 16, UDP
Answer: C
NEW QUESTION 20
Which of the following tools is used to analyze a system and report any unsigned drivers found?
- A. regedit.exe
- B. sigverify.exe
- C. sigverif.exe
- D. msconfig
Answer: C
NEW QUESTION 21
......
100% Valid and Newest Version GCIA Questions & Answers shared by 2passeasy, Get Full Dumps HERE: https://www.2passeasy.com/dumps/GCIA/ (New 508 Q&As)
