It is more faster and easier to pass the Fortinet NSE6_FNC-8.5 exam by using Vivid Fortinet Fortinet NSE 6 - FortiNAC 8.5 questuins and answers. Immediate access to the Refresh NSE6_FNC-8.5 Exam and find the same core area NSE6_FNC-8.5 questions with professionally verified answers, then PASS your exam with a high score now.
Free NSE6_FNC-8.5 Demo Online For Fortinet Certifitcation:
NEW QUESTION 1
Which connecting endpoints are evaluated against all enabled device profiling rules?
- A. All hosts, each time they connect
- B. Rogues devices, only when they connect for the first time
- C. Known trusted devices each time they change location
- D. Rogues devices, each time they connect
Answer: D
NEW QUESTION 2
What would happen if a port was placed in both the Forced Registration and the Forced Remediation port groups?
- A. Only rogue hosts would be impacted.
- B. Both enforcement groups cannot contain the same port.
- C. Only al-risk hosts would be impacted.
- D. Both types of enforcement would be applied.
Answer: A
NEW QUESTION 3
Refer to the exhibit, and then answer the question below.
Which host is rogue?
- A. 1
- B. 3
- C. 2
- D. 4
Answer: C
NEW QUESTION 4
Which two methods can be used to gather a list of installed applications and application details from a host? (Choose two)
- A. Portal page on-boarding options
- B. Application layer traffic inspection
- C. Agent technology
- D. MDM integration
Answer: AB
NEW QUESTION 5
Which command line shell and scripting language does FortiNAC use for WinRM?
- A. Linux
- B. Bash
- C. DOS
- D. Powershell
Answer: D
NEW QUESTION 6
Refer to the exhibit.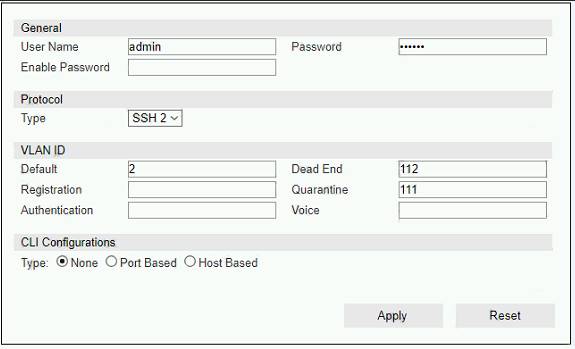
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what will occur?
- A. No VLAN change is performed
- B. The host is moved to a default isolation VLAN.
- C. The host is disabled.
- D. The host is moved to VLAN 111.
Answer: A
NEW QUESTION 7
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
- A. The host is provisioned based on the default access defined by the point of connection.
- B. The host is provisioned based on the network access policy.
- C. The host is isolated.
- D. The host is administratively disabled.
Answer: D
NEW QUESTION 8
Which three circumstances trigger Layer 2 polling of infrastructure devices? (Choose three.)
- A. Manual polling
- B. Scheduled poll timings
- C. A failed Layer 3 poll
- D. A matched security policy
- E. Linkup and Linkdown traps
Answer: BC
NEW QUESTION 9
Which three of the following are components of a security rule? (Choose three.)
- A. Security String
- B. Methods
- C. Action
- D. User or host profile
- E. Trigger
Answer: ABD
NEW QUESTION 10
......
P.S. Dumps-files.com now are offering 100% pass ensure NSE6_FNC-8.5 dumps! All NSE6_FNC-8.5 exam questions have been updated with correct answers: https://www.dumps-files.com/files/NSE6_FNC-8.5/ (30 New Questions)
