Cause all that matters here is passing the Oracle 1Z0-821 exam. Cause all that you need is a high score of 1Z0-821 Oracle Solaris 11 System Administrator exam. The only one thing you need to do is downloading Exambible 1Z0-821 exam study guides now. We will not let you down with our money-back guarantee.
Free 1Z0-821 Demo Online For Oracle Certifitcation:
NEW QUESTION 1
You have been asked to do an orderly shutdown on a process with a PID of 1234, with the kill command.
Which command is best?
- A. kill -2 1234
- B. kill -15 1234
- C. kill -9 1234
- D. kill -1 1234
Answer: B
Explanation:
On POSIX-compliant platforms, SIGTERM is the signal sent to a process to request its termination. The symbolic constant for SIGTERM is defined in the header file signal.h. Symbolic signal names are used because signal numbers can vary across platforms, however on the vast majority of systems, SIGTERM is signal #15.
SIGTERM is the default signal sent to a process by the kill or killall commands. It causes the termination of a process, but unlike the SIGKILL signal, it can be caught and interpreted (or ignored) by the process. Therefore, SIGTERM is akin to asking a process to terminate nicely, allowing cleanup and closure of files. For this reason, on many Unix systems during shutdown, init issues SIGTERM to all processes that are not essential to powering off, waits a few seconds, and then issues SIGKILL to forcibly terminate any such processes that remain.
NEW QUESTION 2
You need to install the solaris-desktop group package. Which command would you use to list the set of packages included in that software group?
- A. pkg search
- B. pkg info
- C. pkginfo
- D. pkg contents
Answer: A
Explanation:
Use the pkg search command to search for packages whose data matches the specified pattern.
Like the pkg contents command, the pkg search command examines the contents of packages. While the pkg contents command returns the contents, the pkg search
command returns the names of packages that match the query.
NEW QUESTION 3
Review the ZFS dataset output that is displayed on your system: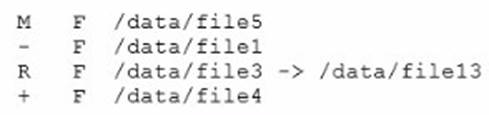
Which four correctly describe the output?
- A. /data/file4 has been added.
- B. The link /data/file3 has been added.
- C. /data/file3 has been renamed to /data/file13.
- D. /data/file4 has been modified and is now larger.
- E. /data/file1 has been deleted.
- F. /data/file1 has been modified and is now smaller.
- G. /data/file5 has been modified.
- H. /data/file3 (a link) has been removed.
Answer: ACEG
Explanation:
A: + Indicates the file/directory was added in the later dataset
C: R Indicates the file/directory was renamed in the later dataset E: - Indicates the file/directory was removed in the later dataset
G: M Indicates the file/directory was modified in the later dataset
Note: Identifying ZFS Snapshot Differences (zfs diff)
You can determine ZFS snapshot differences by using the zfs diff command.
The following table summarizes the file or directory changes that are identified by the zfs diff command.
File or Directory Change Identifier
* File or directory is modified or file or directory link changed M
* File or directory is present in the older snapshot but not in the newer snapshot
—
* File or directory is present in the newer snapshot but not in the older snapshot
+
* File or directory is renamed R
NEW QUESTION 4
You have already generated a 256-bit AES raw key and named the keystore file /mykey. You need to use the key to create an encrypted file system.
Which command should you use to create a ZFS encrypted file system named pool1/encrypt using the /mykey keystore?
- A. zfs create - o encryption = /mykey pool1/encrypt
- B. zfs create - o encryption = 256-ccm - o keysource = raw, file : ///my key pool1/encrypt
- C. zfs create - o encryption = AES keysource = /mykey pool1/encrypt
- D. zfs create - o encryption = on keystore = /mykey pool1/encrypt
Answer: B
Explanation:
Example: Encrypting a ZFS File System by Using a Raw Key
In the following example, an aes-256-ccm encryption key is generated by using the pktool command and is written to a file, /cindykey.file.
# pktool genkey keystore=file outkey=/cindykey.file keytype=aes keylen=256
Then, the /cindykey.file is specified when the tank/home/cindy file system is created.
# zfs create -o encryption=aes-256-ccm -o keysource=raw, file:///cindykey.file tank/home/cindys
NEW QUESTION 5
On which is the open boot prom available?
- A. x86 only
- B. x86 64-Bit only
- C. SPARC only
- D. both x86 and x86 64-Bit
- E. x86, x86 64-Bit and SPARC
Answer: C
Explanation:
No OpenBoot Environment on the Intel Platform. The Intel environment has no OpenBoot PROM or NVRAM. On Intel systems, before the kernel is started, the system is controlled by the basic input/output system (BIOS), the firmware interface on a PC. Therefore, many features provided by OpenBoot are not available on Intel systems.
Note: The Open Boot PROM (OBP) bootloader only exists within SPARC. Before Solaris 10 01/06, the bootloader for Solaris x86 was a Sun customized bootstrap software. After Solaris 10 01/06, it uses GRUB, a well known bootloader that's commonly used in the
Linux world.
With GRUB, it's much easier to make the system dual-boot Linux and Solaris. GRUB extends the capabilities of the bootloader that was not available previously such as the ability to boot from a USB DVD drive. Those who have used Linux will be quite familiar with GRUB and its options.
NEW QUESTION 6
A datalink can best be described as .
- A. a driver for a Network Interface Card
- B. the software connecting the Internet Layer and the Physical Layer
- C. a device that provides Classless Inter-Domain Routing
- D. a logical object used for IP Multipathing
Answer: D
Explanation:
The command dladm is used to configure data-link interfaces in Sun Solaris. A configured data-link is represented in the system as interface that can be used for TCP/IP. Each data- link relies on either a single network device or an link aggregation device to send & recieve packets.
Network interfaces provide the connection between the system and the network. These interfaces are configured over data links, which in turn correspond to instances of hardware devices in the system.
In the current model of the network stack, interfaces and links on the software layer build on the devices in the hardware layer. More specifically, a hardware device instance in the
hardware layer has a corresponding link on the data-link layer and a configured interface on the interface layer. This one-to-one relationship among the network device, its data link, and the IP interface is illustrated in the figure that follows.
Network Stack Showing Network Devices, Links, and Interfaces: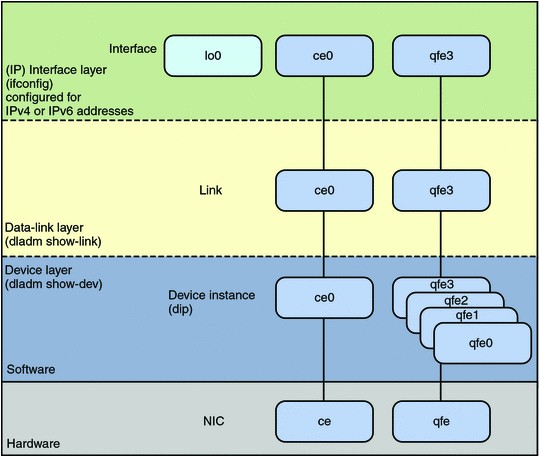
NEW QUESTION 7
You want to deploy Oracle Solaris 11 with the Automated Installer (AI). You need to make sure that your server and network meet the requirements for using AI.
Choose the three options that describe the requirements for using AI.
- A. You can create only one manifest per install servic
- B. If you need more than one manifest create multiple install services.
- C. If two client machines have different architectures and need to be installed with the same version of the Oracle Solaris 11 OS, then create two AI manifests and a single install service.
- D. You need a separate install service for each different client architecture that you plan to install, and for each different version of the Oracle Solaris 11 OS that you plan to install on client systems.
- E. If two client machines have different architectures and need to be installed with different versions of the Oracle Solaris 11 OS, then create two AI manifests and two install services.
- F. The install server needs to be able to access an Oracle Solaris Image Packaging System (IPS) software package repository; the clients do not.
- G. The install server can be either an x86 machine or a SPARC machine.
Answer: BEF
Explanation:
B (not A, not D, Not C): If two client machines need to be installed with the same version of the Oracle Solaris 11 OS but
need to be installed differently in other ways, then create two AI manifests for the AI install service. The different AI manifests can specify different packages to install or a different
slice as the install target, for example.
Note: An AI manifest provides installation instructions.
The AI manifest specifies one or more IPS package repositories where the client retrieves the packages needed to complete the installation. The AI manifest also includes the names of additional packages to install and information such as target installation device and partition information.
F: The install server can be either an x86 machine or a SPARC machine.
NEW QUESTION 8
Which two statements describe the COMSTAR framework available in Oracle Solaris 11?
- A. It converts an Oracle Solaris 11 host into a SCSI target device that can be accessed over a storage network by Linux, Mac OS, or Windows client systems.
- B. iSCSI targets cannot be configured as dump devices.
- C. It provides support for iSCSI devices that use SLP.
- D. It is used to connect to Fibre Channel or iSCSI Storage Area Network (SAN) environments.
- E. It provides an upgrade and update path to convert your iSCSI LUNs from Solaris 10 systems.
Answer: AB
Explanation:
A: You can configure Common Multiprotocol SCSI TARget, or COMSTAR, a software
framework that enables you to convert any Oracle Solaris 11 host into a SCSI target device that can be accessed over a storage network by initiator hosts.
This means you can make storage devices on a system available to Linux, Mac OS, or Windows client systems as if they were local storage devices. Supported storage protocols are iSCSI, FC, iSER, and SRP.
B: iSCSI targets cannot be configured as dump devices.
NEW QUESTION 9
A user jack, using a korn shell, requests a directory listing as follows:
jack@solaris:/export/home/jack $ 1s File filea Filea fileb Fileb filec Filec
Which two statements are correct?
- A. The pattern [?i]*a will expand to filea Filea.
- B. The pattern [fF]*a? will expand to [fF] *a?.
- C. The pattern [gfe] * will expand to file filea fileb filec.
- D. The pattern [g-e] * will expand to file filea fileb filec.
- E. The pattern [fF] [a-zA-z] i*e will expand to file.
Answer: AC
Explanation:
A: starting with one single character, second character must be letter i, any characters, ending with letter a.
C: starting with letter e, f, or g, followed by anything.
NEW QUESTION 10
Which three of the components could be used in a ZFS storage pool, but are not recommended configurations?
- A. A file on a UFS file system
- B. A Veritas Volume Manager (VxVM) volume
- C. A LUN In a hardware RAID array
- D. A disk slice from an SMI labeled disk
- E. A Solaris Volume Manager (SVM) volume
- F. An EFI labeled disk
Answer: ABE
Explanation:
A: ZFS also allows you to use UFS files as virtual devices in your storage pool. This feature is aimed primarily at testing and enabling simple experimentation, not for production use. The reason is that any use of files relies on the underlying file system for consistency. If you create a ZFS pool backed by files on a UFS file system, then you are implicitly relying on UFS to guarantee correctness and synchronous semantics.
However, files can be quite useful when you are first trying out ZFS or experimenting with more complicated layouts when not enough physical devices are present. All files must be specified as complete paths and must be at least 64 Mbytes in size.
B, E: You can construct logical devices for ZFS using volumes presented by software-
based volume managers, such as Solaris Volume Manager (SVM) or Veritas Volume Manager (VxVM). However, these configurations are not recommended. While ZFS functions properly on such devices, less-than-optimal performance might be the result.
NEW QUESTION 11
View the Exhibit.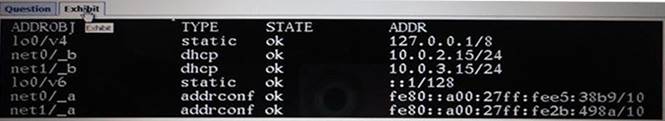
After Installing the OS, you need to verify the network interface information. Which command was used to display the network interface information in the exhibit?
- A. ifconfiq –a
- B. ipadm show-addr
- C. svcs –1 network/physical
- D. netstat –a
Answer: B
Explanation:
'ipadm show-addr' displays all the configured addresses on the system. Example:
# ipadm show-addr
ADDROBJ TYPE STATE ADDR
lo0/v4 static ok 127.0.0.1/8 lo0/v6 static ok ::1/128
NEW QUESTION 12
Which two are user definable OpenBoot parameters that can be set in the OpenBoot PROM?
- A. IP address for the system console
- B. Host ID
- C. System date and time
- D. Default boot device
- E. Verbose hardware diagnostics
- F. Powering off the hardware
Answer: DE
Explanation:
The NVRAM chip stores user-definable system parameters, also referred to as NVRAM variables or EEPROM parameters. The parameters allow administrators to control
variables such as the default boot device and boot command. The NVRAM also contains writeable areas for user-controlled diagnostics, macros, and device aliases. NVRAM is where the system identification information is stored, such as the host ID, Ethernet address, and time-of-day (TOD) clock.
Examples of NVRAM variables:
Variable Default Description boot-device disk or net The device from which to start up.
diag-device net The diagnostic startup source device.
diag-file Empty string Arguments passed to the startup program in diagnostic mode. diag-switch? false Whether to run in diagnostic mode
NEW QUESTION 13
Which two statements are true concerning the creation of user accounts by using the useradd command?
- A. By default, it will create the user's home directory.
- B. New user accounts are unlocked but must change their password at their first login.
- C. New user accounts are in a pending activation state until a password is assigned to them.
- D. By default, a new group will be added for each new user account.
- E. By default, the UID of a new user account will be the next available number above the highest number currently assigned.
- F. By default, the UID of a new user account with be the lowest available unused number for nonsystem accounts.
Answer: CE
NEW QUESTION 14
Solaris 11 includes a redesigned software packaging model: the Image Packaging system.
Which three describe advantages of the Image Packaging System over the previous Solaris 10 SVR4 packaging model?
- A. Eliminates patching of the software package
- B. Makes the patching process more efficient with less downtime
- C. Eliminates OS version upgrade
- D. Allows for the installation of the OS without a local DVD or installation server
- E. Allows the use of a repository mirror to speed up package operation
- F. Allows users to publish their own software package in a software repository
Answer: AEF
NEW QUESTION 15
You start to execute a program by using the following command:
~/bigscript &
You then determine that the process is not behaving as expected, and decide that you need to terminate the process.
Based on the information shown below, what is the process number you should terminate?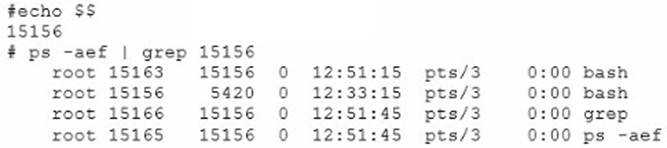
- A. 15163
- B. 15156
- C. 15166
- D. 15165
Answer: A
Explanation:
From the output exhibit we can deduce that the shell has id 15156. It has spawned three subprocesses:
grep: id 15166
ps –aef 15165
The remaining 15163 must be the subshell (see note below). This is the id of the process which should be terminated.
NEW QUESTION 16
Which two options describe how to override the default boot behavior of an Oracle Solaris 11 SPARC system to boot the system to the single-user milestone?
- A. from the ok prompt, issue this command: boot -m milestone=single-user
- B. From the ok prompt, issue this command: boot -m milestone/single-user
- C. From the ok prompt, issue this command: boot -milestone=single-user
- D. From the ok promp
- E. issue this command:boot -s
- F. From from the ok prompt, issue this command:boot -m milestone=s
Answer: AD
Explanation:
By default, Solaris will boot to the pseudo milestone “all” and start all services. This behaviour can be changed at boot time using either “-s” to reach single-user, or the new SMF option “-m milestone=XXX” (see kernel(1M) for a list of the bootable milestones) to select an explicit milestone.
Note: boot -s is the same as: boot -m milestone=single-user
with the difference being that the former is a lot less to type and is what most SysAdmins will be familiar with.
NEW QUESTION 17
You are going to create live zones on you server. Disk space is critical on this server so you need to reduce the amount of disk space required for these zones. Much of the data required for each of these zones is identical, so you want to eliminate the duplicate copies of data and store only data that is unique to each zone.
Which two options provide a solution for eliminating the duplicate copies of data that is common between all of these zones?
- A. Create the zones by using sparse root zones.
- B. Set the dedup property to on and the dedupratio to at least 1.5 for the zpool.Create a separate ZFS file system for each zone in the zpool.
- C. Put all of the zones in the same ZFS file system and set the dedupratio property for the ZFS file system to at least 1.5.
- D. Put all of the zones in the same ZFS file system and set the dedup property for the file system to on.
- E. Put each zone in a separate ZFS file system within the same zpoo
- F. Set the dedup property to on for each ZFS file system.
Answer: DE
Explanation:
n Oracle Solaris 11, you can use the deduplication (dedup) property to remove redundant data from your ZFS file systems. If a file system has the dedup property enabled, duplicate data blocks are removed synchronously. The result is that only unique data is stored, and common components are shared between files.
NEW QUESTION 18
After installing the OS, you boot the system and notice that the syslogd daemon is not
accepting messages from remote systems.
Which two options should you select to modify the syslogd daemon configuration so that it accepts messages from remote systems?
- A. svccfg -s svc:/system/system -log setprop start/exec= “syslogd -t”Restart the syslogd daemon.
- B. Set the following parameter in the /etc/syslogd.conf file: LOG_FROM_REMOTE= YESRestart the syslogd daemon.
- C. svcadm enable svc:/system/system -log/config/log_from_remoteRestart the syslogd daemon.
- D. svccfg -s svc:/system/system-log setprop config/log_from_remote=trueRestart the syslogd daemon.
- E. Set the following parameter in the /etc/default/syslogd file: LOG_FROM_REMOTE=YESRestart the syslogd daemon.
Answer: BD
Explanation:
B: The /etc/default/syslogd file contains the following default parameter settings. See FILES.
LOG_FROM_REMOTE
Specifies whether remote messages are logged. LOG_FROM_REMOTE=NO is equivalent to the -t command-line option. The default value for LOG_FROM_REMOTE is YES.
NEW QUESTION 19
How are operating system updates distributed in the Oracle Solaris 11 environment?
- A. Updates are only available to customers with an active support contrac
- B. The updates are distributed through the My Oracle Support web portal and installed in a central locatio
- C. All software packages are then updated manually from the command line using the smpatch command.
- D. Patches are download from http: //support.oracle.com either automatically or manuall
- E. All software packages are then updated manually from the command line using the smpatch or patchadd commands.
- F. Software updates are published as packages to a repositor
- G. All software packages are then updated manually from the command line using the pkg command.
- H. Software updates, published as packages to an OS imag
- I. All software packages are then updated manually from the command line using the pkg command.
Answer: C
Explanation:
* Updating all of the packages on your installed system – To update all of the packages on your system that have available updates, use the pkg update command, as follows:
# pkg update
Running this command updates packages that you might not otherwise consider updating, for example, kernel components and other low-level system packages.
* Adding or updating individual packages – To add individual software packages, use the pkg install command. Any dependent packages are also updated at the same time.
* install package updates that deliver fixes– A pkg update operation might include bug fixes, so the operation is similar to applying a specific patch or patches in previous Oracle Solaris releases.
Note: The IPS interfaces first check for updates for currently installed packages before retrieving them via the network. By default, interfaces check repository catalogs in the following locations:
* The default installation repository at pkg.oracle.com/solaris/release.
* The support repository in My Oracle Support. This repository is restricted to users with Oracle Solaris 11 Express support contracts, and it contains packages with the latest bug fixes. For this reason, a support contract must be purchased for production deployments.
NEW QUESTION 20
The /etc/hosts file can be best described as .
- A. a local database of host names for rlogin, rsh, and rep
- B. the configuration file for the host name of the system
- C. a local database of information for the uname command
- D. the configuration file for the Domain Name Service (DNS)
- E. a local database of host names and their associated IP addresses
Answer: E
Explanation:
As your machine gets started, it will need to know the mapping of some hostnames to IP addresses before DNS can be referenced. This mapping is kept in the /etc/hosts file. In the absence of a name server, any network program on your system consults this file to determine the IP address that corresponds to a host name.
NEW QUESTION 21
The following information is displayed about the compress/zjp software package, which Is currently installed on this system:
NAME (PUBLISHER)VERSIONIFO
Compress/zip3.1.2-0.175.0.0.0.0.537if-
NAMEVERSIONDATECOMMENT
Compress/zip3.109 Dec 2011 04:50:38 ESTNone
Which statement describes the information that is displayed tor the compress/zip software package?
- A. This package cannot be removed.
- B. This package can be updated to a new version when the new version of the package becomes available.
- C. This package cannot be updated.
- D. This package can be updated to version 3.1.3 but not 3.2.
- E. This package cannot be downgraded to version 3.1.1.
Answer: B
Explanation:
An “f” in the F column indicates the package is frozen. If a package is frozen, you can only install or update to packages that match the frozen version.
Note: The “i” in the I column indicates that these packages are installed in this image. Adding and Updating Oracle Solaris 11 Software Packages, Showing Package Install State
Information
NEW QUESTION 22
A user on the system has started a process, but it needs to be terminated. The process ID was determined as follows:
pgrep userprogram l5317
The user attempted to terminate the program as follows: pkill 15317
This command runs without an error message, and the process continues to run. What is the issue?
- A. You need to run the pkill command with the process name.
- B. You need to switch to super user to kill the process.
- C. You need to run the ps command to get more information.
- D. You need to run the prstat command to get more information.
Answer: B
Explanation:
You can use the pgrep and pkill commands to identify and stop command processes that you no longer want to run. These commands are useful when you mistakenly start a process that takes a long time to run.
To terminate a process:
Type pgrep to find out the PID(s) for the process(es). Type pkill followed by the PID(s).
You can kill any process that you own. Superuser can kill any process in the system except for those processes with process IDs of 0, 1, 2, 3, and 4. Killing these processes most likely
will crash the system.
NEW QUESTION 23
You are troubleshooting interface net3 and you enter the following sequence of commands: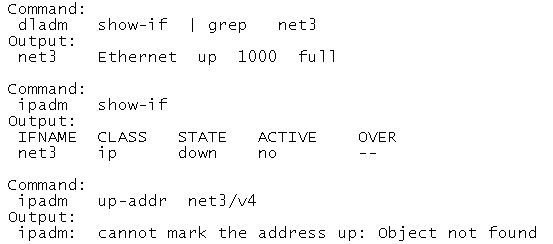
Your next command should be:
- A. ipadm up-addr net3/v4
- B. ipadm enable-if -T net3
- C. <ipadm create-vnic -a 192.168.1.25/24 net3/v4
- D. ipadm create-ip -T static -a 192.168.1.25/24 -n net3
- E. ipadm create-addr -T static -a 192.168.1.25/24 net3
Answer: E
Explanation:
If you are assigning a static IP address, use the following syntax:
# ipadm create-addr -T static -a address addrobj
where addrobj uses the naming format interface/user-defined-string, such as e1000g0/v4globalz.
Note:
create-addr [-t] -T static [-d] -a {local | remote}=addr[/prefixlen], ... addrobj
Creates a static IPv4 or IPv6 address on the interface specified in addrobj. If the interface on which the address is created is not plumbed, this subcommand will implicitly plumb the interface. The created static address will be identified by addrobj.
By default, a configured address will be marked up, so that it can be used as a source or destination of or for outbound and inbound packets.
NEW QUESTION 24
......
P.S. Easily pass 1Z0-821 Exam with 243 Q&As Dumps-hub.com Dumps & pdf Version, Welcome to Download the Newest Dumps-hub.com 1Z0-821 Dumps: https://www.dumps-hub.com/1Z0-821-dumps.html (243 New Questions)
