Exam Code: CS0-002 (Practice Exam Latest Test Questions VCE PDF)
Exam Name: CompTIA Cybersecurity Analyst (CySA+) Certification Exam
Certification Provider: CompTIA
Free Today! Guaranteed Training- Pass CS0-002 Exam.
Online CS0-002 free questions and answers of New Version:
NEW QUESTION 1
A security analyst on the threat-hunting team has developed a list of unneeded, benign services that are currently running as part of the standard OS deployment for workstations. The analyst will provide this list to the operations team to create a policy that will automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
- A. To create a system baseline
- B. To reduce the attack surface
- C. To optimize system performance
- D. To improve malware detection
Answer: B
NEW QUESTION 2
Which of the following BEST articulates the benefit of leveraging SCAP in an organization’s cybersecurity analysis toolset?
- A. It automatically performs remedial configuration changes to enterprise security services
- B. It enables standard checklist and vulnerability analysis expressions for automation
- C. It establishes a continuous integration environment for software development operations
- D. It provides validation of suspected system vulnerabilities through workflow orchestration
Answer: B
NEW QUESTION 3
As a proactive threat-hunting technique, hunters must develop situational cases based on likely attack scenarios derived from the available threat intelligence information. After forming the basis of the scenario, which of the following may the threat hunter construct to establish a framework for threat assessment?
- A. Critical asset list
- B. Threat vector
- C. Attack profile
- D. Hypothesis
Answer: A
NEW QUESTION 4
A company recently experienced a break-in whereby a number of hardware assets were stolen through unauthorized access at the back of the building. Which of the following would BEST prevent this type of theft from occurring in the future?
- A. Motion detection
- B. Perimeter fencing
- C. Monitored security cameras
- D. Badged entry
Answer: A
NEW QUESTION 5
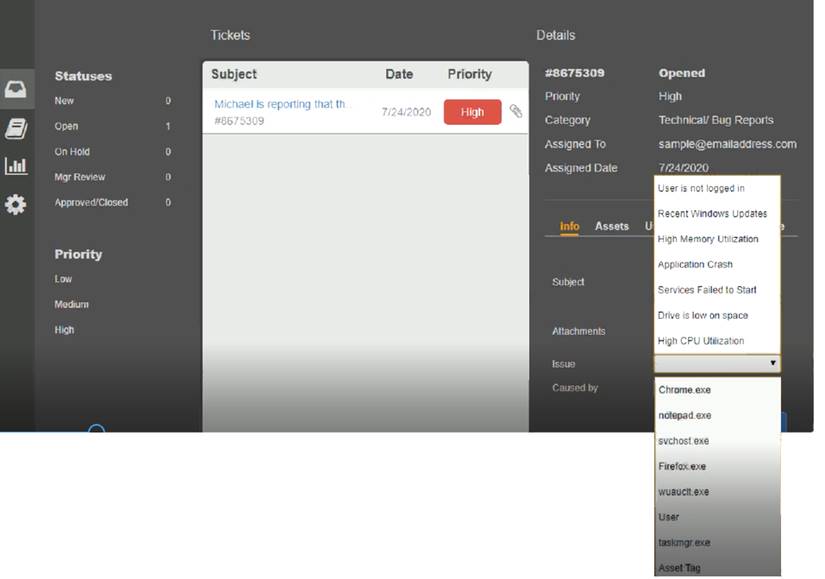
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue. INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button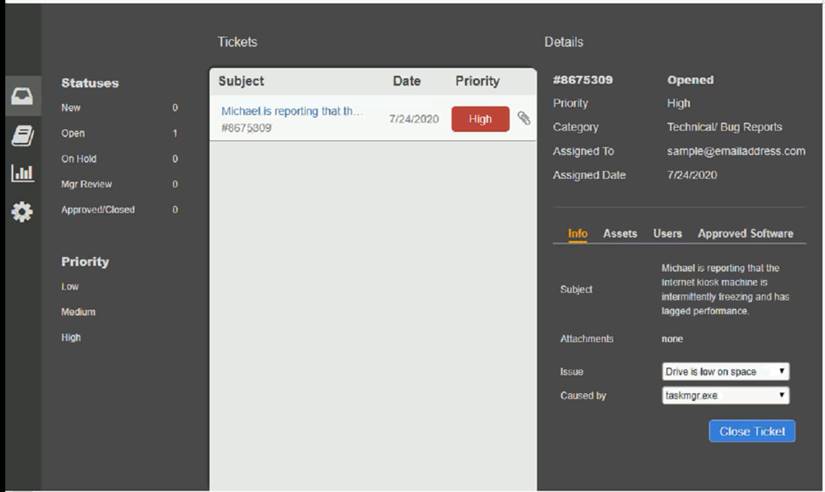
- A. Mastered
- B. Not Mastered
Answer: A
Explanation: 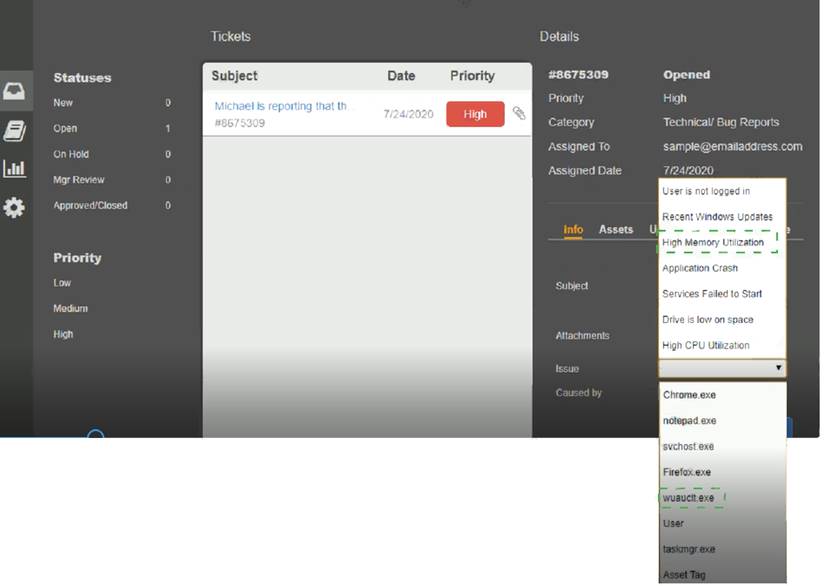
NEW QUESTION 6
Which of the following software security best practices would prevent an attacker from being able to run arbitrary SQL commands within a web application? (Choose two.)
- A. Parameterized queries
- B. Session management
- C. Input validation
- D. Output encoding
- E. Data protection
- F. Authentication
Answer: AC
NEW QUESTION 7
A security analyst is providing a risk assessment for a medical device that will be installed on the corporate network. During the assessment, the analyst discovers the device has an embedded operating system that will be at the end of its life in two years. Due to the criticality of the device, the security committee makes a risk- based policy decision to review and enforce the vendor upgrade before the end of life is reached.
Which of the following risk actions has the security committee taken?
- A. Risk exception
- B. Risk avoidance
- C. Risk tolerance
- D. Risk acceptance
Answer: D
NEW QUESTION 8
An organization has several system that require specific logons Over the past few months, the security analyst has noticed numerous failed logon attempts followed by password resets. Which of the following should the analyst do to reduce the occurrence of legitimate failed logons and password resets?
- A. Use SSO across all applications
- B. Perform a manual privilege review
- C. Adjust the current monitoring and logging rules
- D. Implement multifactor authentication
Answer: B
NEW QUESTION 9
A security analyst is investigating a system compromise. The analyst verities the system was up to date on OS patches at the time of the compromise. Which of the following describes the type of vulnerability that was MOST likely expiated?
- A. Insider threat
- B. Buffer overflow
- C. Advanced persistent threat
- D. Zero day
Answer: D
NEW QUESTION 10
An analyst is investigating an anomalous event reported by the SOC After reviewing the system logs the analyst identifies an unexpected addition of a user with root-level privileges on the endpoint. Which of the following data sources will BEST help the analyst to determine whether this event constitutes an incident?
- A. Patching logs
- B. Threat feed
- C. Backup logs
- D. Change requests
- E. Data classification matrix
Answer: D
NEW QUESTION 11
A cybersecurity analyst needs to rearchitect the network using a firewall and a VPN server to achieve the highest level of security To BEST complete this task, the analyst should place the:
- A. firewall behind the VPN server
- B. VPN server parallel to the firewall
- C. VPN server behind the firewall
- D. VPN on the firewall
Answer: B
NEW QUESTION 12
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output: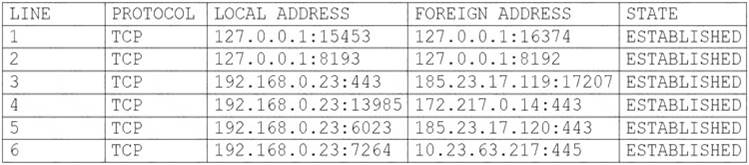
Which of the following lines indicates the computer may be compromised?
- A. Line 1
- B. Line 2
- C. Line 3
- D. Line 4
- E. Line 5
- F. Line 6
Answer: D
NEW QUESTION 13
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team’s NEXT step during the detection phase of this response process?
- A. Escalate the incident to management, who will then engage the network infrastructure team to keep them informed.
- B. Depending on system criticality, remove each affected device from the network by disabling wired and wireless connections.
- C. Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses.
- D. Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
Answer: D
NEW QUESTION 14
A security analyst has been alerted to several emails that snow evidence an employee is planning malicious activities that involve employee Pll on the network before leaving the organization. The security analysis BEST response would be to coordinate with the legal department and:
- A. the public relations department
- B. senior leadership
- C. law enforcement
- D. the human resources department
Answer: D
NEW QUESTION 15
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL: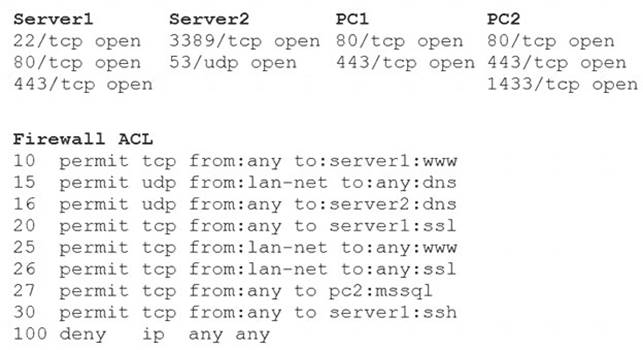
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
- A. PC1
- B. PC2
- C. Server1
- D. Server2
- E. Firewall
Answer: B
NEW QUESTION 16
As part of an exercise set up by the information security officer, the IT staff must move some of the network systems to an off-site facility and redeploy them for testing. All staff members must ensure their respective systems can power back up and match their gold image. If they find any inconsistencies, they must formally document the information.
Which of the following BEST describes this test?
- A. Walk through
- B. Full interruption
- C. Simulation
- D. Parallel
Answer: C
NEW QUESTION 17
Risk management wants IT to implement a solution that will permit an analyst to intercept, execute, and analyze potentially malicious files that are downloaded from the Internet.
Which of the following would BEST provide this solution?
- A. File fingerprinting
- B. Decomposition of malware
- C. Risk evaluation
- D. Sandboxing
Answer: D
NEW QUESTION 18
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following: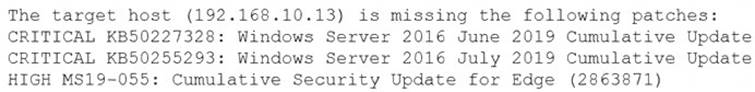
Tool B reported the following:
Which of the following BEST describes the method used by each tool? (Choose two.)
- A. Tool A is agent based.
- B. Tool A used fuzzing logic to test vulnerabilities.
- C. Tool A is unauthenticated.
- D. Tool B utilized machine learning technology.
- E. Tool B is agent based.
- F. Tool B is unauthenticated.
Answer: CE
NEW QUESTION 19
A finance department employee has received a message that appears to have been sent from the Chief Financial Officer (CFO) asking the employee to perform a wife transfer Analysis of the email shows the message came from an external source and is fraudulent. Which of the following would work BEST to improve the likelihood of employees quickly recognizing fraudulent emails?
- A. Implementing a sandboxing solution for viewing emails and attachments
- B. Limiting email from the finance department to recipients on a pre-approved whitelist
- C. Configuring email client settings to display all messages in plaintext when read
- D. Adding a banner to incoming messages that identifies the messages as external
Answer: D
NEW QUESTION 20
A cyber-incident response analyst is investigating a suspected cryptocurrency miner on a company's server. Which of the following is the FIRST step the analyst should take?
- A. Create a full disk image of the server's hard drive to look for the file containing the malware.
- B. Run a manual antivirus scan on the machine to look for known malicious software.
- C. Take a memory snapshot of the machine to capture volatile information stored in memory.
- D. Start packet capturing to look for traffic that could be indicative of command and control from the miner.
Answer: D
NEW QUESTION 21
......
100% Valid and Newest Version CS0-002 Questions & Answers shared by DumpSolutions.com, Get Full Dumps HERE: https://www.dumpsolutions.com/CS0-002-dumps/ (New 186 Q&As)
