Validated of SSCP exam engine materials and testing software for ISC2 certification for examinee, Real Success Guaranteed with Updated SSCP pdf dumps vce Materials. 100% PASS System Security Certified Practitioner (SSCP) exam Today!
Online ISC2 SSCP free dumps demo Below:
NEW QUESTION 1
How many bits of a MAC address uniquely identify a vendor, as provided by the IEEE?
- A. 6 bits
- B. 12 bits
- C. 16 bits
- D. 24 bits
Answer: D
Explanation:
The MAC address is 48 bits long, 24 of which identify the vendor, as provided by the IEEE. The other 24 bits are provided by the vendor.
A media access control address (MAC address) is a unique identifier assigned to network interfaces for communications on the physical network segment. MAC addresses are used for numerous network technologies and most IEEE 802 network technologies, including Ethernet. Logically, MAC addresses are used in the media access control protocol sublayer of the OSI reference model.
MAC addresses are most often assigned by the manufacturer of a network interface card (NIC) and are stored in its hardware, such as the card's read-only memory or some other firmware mechanism. If assigned by the manufacturer, a MAC address usually encodes the manufacturer's registered identification number and may be referred to as the burned-in address. It may also be known as an Ethernet hardware address (EHA), hardware address or physical address. This is can be contrasted to a programmed address, where the host device issues commands to the NIC to use an arbitrary address. An example is many SOHO routers, where the ISP grants access to only one MAC address (used previously to inserting the router) so the router must use that MAC address on its Internet-facing NIC. Therefore the router administrator configures a MAC address to override the burned-in one.
A network node may have multiple NICs and each must have one unique MAC address per NIC.
See diagram below from Wikipedia showing the format of a MAC address. : MAC Address format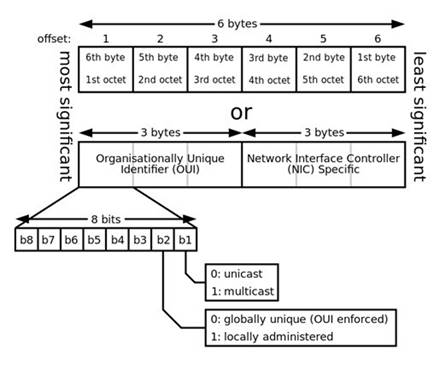
C:\Users\MCS\Desktop\1.jpg
Reference(s) used for this question: http://en.wikipedia.org/wiki/MAC_address
NEW QUESTION 2
What ISO/OSI layer do switches primarily operate at?
Do take note that this question makes reference to a plain vanilla switch and not one of the smart switches that is available on the market today.
- A. Physical layer
- B. Network layer
- C. Data link layer
- D. Session layer
Answer: C
Explanation:
Switches primarily operate at the data link layer (layer 2), although intelligent, extremely fast Layer 3 switching techniques are being more frequently used.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 111).
NEW QUESTION 3
Which of the following protection devices is used for spot protection within a few inches of the object, rather than for overall room security monitoring?
- A. Wave pattern motion detectors
- B. Capacitance detectors
- C. Field-powered devices
- D. Audio detectors
Answer: B
Explanation:
Capacitance detectors monitor an electrical field surrounding the object being monitored. They are used for spot protection within a few inches of the object, rather than for overall room security monitoring used by wave detectors. Penetration of this field changes the electrical capacitance of the field enough to generate and alarm. Wave pattern motion detectors generate a frequency wave pattern and send an alarm if the pattern is disturbed as it is reflected back to its receiver. Field-powered devices are a type of personnel access control devices. Audio detectors simply monitor a room for any abnormal sound wave generation and trigger an alarm.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 10: Physical security (page 344).
NEW QUESTION 4
Physically securing backup tapes from unauthorized access is obviously a security concern and is considered a function of the:
- A. Operations Security Domain.
- B. Operations Security Domain Analysis.
- C. Telecommunications and Network Security Domain.
- D. Business Continuity Planning and Disater Recovery Planning.
Answer: A
Explanation:
Physically securing the tapes from unauthorized access is obviously a security concern and is considered a function of the Operations Security Domain. Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 71.
NEW QUESTION 5
How is Annualized Loss Expectancy (ALE) derived from a threat?
- A. ARO x (SLE - EF)
- B. SLE x ARO
- C. SLE/EF
- D. AV x EF
Answer: B
Explanation:
Three steps are undertaken in a quantitative risk assessment:
Initial management approval
Construction of a risk assessment team, and
The review of information currently available within the organization.
There are a few formulas that you MUST understand for the exam. See them below: SLE (Single Loss Expectancy)
Single loss expectancy (SLE) must be calculated to provide an estimate of loss. SLE is defined as the difference between the original value and the remaining value of an asset after a single exploit.
The formula for calculating SLE is as follows: SLE = asset value (in $) ?? exposure factor (loss due to successful threat exploit, as a %)
Losses can include lack of availability of data assets due to data loss, theft, alteration, or denial of service (perhaps due to business continuity or security issues).
ALE (Annualized Loss Expectancy)
Next, the organization would calculate the annualized rate of occurrence (ARO). This is done to provide an accurate calculation of annualized loss expectancy (ALE).
ARO is an estimate of how often a threat will be successful in exploiting a vulnerability over the period of a year.
When this is completed, the organization calculates the annualized loss expectancy (ALE). The ALE is a product of the yearly estimate for the exploit (ARO) and the loss in value of an asset after an SLE.
The calculation follows ALE = SLE x ARO
Note that this calculation can be adjusted for geographical distances using the local annual frequency estimate (LAFE) or the standard annual frequency estimate (SAFE). Given that there is now a value for SLE, it is possible to determine what the organization should spend, if anything, to apply a countermeasure for the risk in question.
Remember that no countermeasure should be greater in cost than the risk it mitigates, transfers, or avoids.
Countermeasure cost per year is easy and straightforward to calculate. It is simply the cost of the countermeasure divided by the years of its life (i.e., use within the organization). Finally, the organization is able to compare the cost of the risk versus the cost of the countermeasure and make some objective decisions regarding its countermeasure selection.
The following were incorrect answers: All of the other choices were incorrect.
The following reference(s) were used for this quesiton:
Hernandez CISSP, Steven (2012-12-21). Official (ISC)2 Guide to the CISSP CBK, Third Edition ((ISC)2 Press) (Kindle Locations 10048-10069). Auerbach Publications. Kindle Edition.
NEW QUESTION 6
Which of the following statements pertaining to disk mirroring is incorrect?
- A. Mirroring offers better performance in read operations but writing hinders system performance.
- B. Mirroring is a hardware-based solution only.
- C. Mirroring offers a higher fault tolerance than parity.
- D. Mirroring is usually the less cost-effective solution.
Answer: B
Explanation:
With mirroring, the system writes the data simultaneously to separate drives
or arrays.
The advantage of mirroring are minimal downtime, simple data recovery, and increased performance in reading from the disk.
The disadvantage of mirroring is that both drives or disk arrays are processing in the writing to disks function, which can hinder system performance.
Mirroring has a high fault tolerance and can be implemented either through a hardware RAID controller or through the operating system. Since it requires twice the disk space than actual data, mirroring is the less cost-efficient data redundancy strategy.
Source: SWANSON, Marianne, & al., National Institute of Standards and Technology (NIST), NIST Special Publication 800-34, Contingency Planning Guide for Information Technology Systems, December 2001 (page 45).
NEW QUESTION 7
Which of the following is an example of a passive attack?
- A. Denying services to legitimate users
- B. Shoulder surfing
- C. Brute-force password cracking
- D. Smurfing
Answer: B
Explanation:
Shoulder surfing is a form of a passive attack involving stealing passwords, personal identification numbers or other confidential information by looking over someone's shoulder. All other forms of attack are active attacks, where a threat makes a modification to the system in an attempt to take advantage of a vulnerability.
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw- Hill/Osborne, 2002, chapter 3: Security Management Practices (page 63).
NEW QUESTION 8
What security problem is most likely to exist if an operating system permits objects to be used sequentially by multiple users without forcing a refresh of the objects?
- A. Disclosure of residual data.
- B. Unauthorized obtaining of a privileged execution state.
- C. Denial of service through a deadly embrace.
- D. Data leakage through covert channels.
Answer: A
Explanation:
This question is asking you to consider the effects of object reuse. Object reuse is "reassigning to subject media that previously contained information. Object reuse is a security concern because if insufficient measures were taken to erase the information on the media, the information may be disclosed to unauthorized personnel."
This concept relates to Security Architecture and Design, because it is in level C2: Controlled Access Protection, of the Orange Book, where "The object reuse concept must be invoked, meaning that any medium holding data must not contain any remnants of information after it is release for another subject to use."
REFERENCE:
AIO Version 5 (Shon Harris), page 360 and
TIPTON, Hal, (ISC)2, Introduction to the CISSP Exam presentation.
NEW QUESTION 9
Which of the following IEEE standards defines the token ring media access method?
- A. 802.3
- B. 802.11
- C. 802.5
- D. 802.2
Answer: D
Explanation:
The IEEE 802.5 standard defines the token ring media access method. 802.3 refers to Ethernet's CSMA/CD, 802.11 refers to wireless communications and 802.2 refers to the logical link control.
Source: KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 3: Telecommunications and Network Security (page 109).
NEW QUESTION 10
Which of the following is not a one-way hashing algorithm?
- A. MD2
- B. RC4
- C. SHA-1
- D. HAVAL
Answer: B
Explanation:
RC4 was designed by Ron Rivest of RSA Security in 1987. While it is officially termed "Rivest Cipher 4", the RC acronym is alternatively understood to stand for "Ron's Code" (see also RC2, RC5 and RC6).
RC4 was initially a trade secret, but in September 1994 a description of it was anonymously posted to the Cypherpunks mailing list. It was soon posted on the sci.crypt newsgroup, and from there to many sites on the Internet. The leaked code was confirmed to be genuine as its output was found to match that of proprietary software using licensed RC4. Because the algorithm is known, it is no longer a trade secret. The name RC4 is trademarked, so RC4 is often referred to as ARCFOUR or ARC4 (meaning alleged RC4) to avoid trademark problems. RSA Security has never officially released the algorithm; Rivest has, however, linked to the English Wikipedia article on RC4 in his own course notes. RC4 has become part of some commonly used encryption protocols and standards, including WEP and WPA for wireless cards and TLS.
The main factors in RC4's success over such a wide range of applications are its speed and simplicity: efficient implementations in both software and hardware are very easy to develop.
The following answer were not correct choices:
SHA-1 is a one-way hashing algorithms. SHA-1 is a cryptographic hash function designed by the United States National Security Agency and published by the United States NIST as a U.S. Federal Information Processing Standard. SHA stands for "secure hash algorithm".
The three SHA algorithms are structured differently and are distinguished as SHA-0, SHA- 1, and SHA-2. SHA-1 is very similar to SHA-0, but corrects an error in the original SHA hash specification that led to significant weaknesses. The SHA-0 algorithm was not adopted by many applications. SHA-2 on the other hand significantly differs from the SHA- 1 hash function.
SHA-1 is the most widely used of the existing SHA hash functions, and is employed in several widely used security applications and protocols. In 2005, security flaws were identified in SHA-1, namely that a mathematical weakness might exist, indicating that a stronger hash function would be desirable. Although no successful attacks have yet been reported on the SHA-2 variants, they are algorithmically similar to SHA-1 and so efforts are underway to develop improved alternatives. A new hash standard, SHA-3, is currently under development ?? an ongoing NIST hash function competition is scheduled to end with the selection of a winning function in 2012.
SHA-1 produces a 160-bit message digest based on principles similar to those used by Ronald L. Rivest of MIT in the design of the MD4 and MD5 message digest algorithms, but has a more conservative design.
MD2 is a one-way hashing algorithms. The MD2 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1989. The algorithm is optimized for 8-bit computers. MD2 is specified in RFC 1319. Although MD2 is no longer considered secure, even as of 2010 it remains in use in public key infrastructures as part of certificates generated with MD2 and RSA.
Haval is a one-way hashing algorithms. HAVAL is a cryptographic hash function. Unlike MD5, but like most modern cryptographic hash functions, HAVAL can produce hashes of different lengths. HAVAL can produce hashes in lengths of 128 bits, 160 bits, 192 bits, 224 bits, and 256 bits. HAVAL also allows users to specify the number of rounds (3, 4, or 5) to be used to generate the hash.
The following reference(s) were used for this question:
SHIREY, Robert W., RFC2828: Internet Security Glossary, may 2000.
and https://en.wikipedia.org/wiki/HAVAL and
https://en.wikipedia.org/wiki/MD2_%28cryptography%29 and
https://en.wikipedia.org/wiki/SHA-1
NEW QUESTION 11
In regards to information classification what is the main responsibility of information (data) owner?
- A. determining the data sensitivity or classification level
- B. running regular data backups
- C. audit the data users
- D. periodically check the validity and accuracy of the data
Answer: A
Explanation:
Making the determination to decide what level of classification the information requires is the main responsibility of the data owner.
The data owner within classification is a person from Management who has been entrusted with a data set that belong to the company. It could be for example the Chief Financial Officer (CFO) who has been entrusted with all financial date or it could be the Human Resource Director who has been entrusted with all Human Resource data. The information owner will decide what classification will be applied to the data based on Confidentiality, Integrity, Availability, Criticality, and Sensitivity of the data.
The Custodian is the technical person who will implement the proper classification on objects in accordance with the Data Owner. The custodian DOES NOT decide what classification to apply, it is the Data Owner who will dictate to the Custodian what is the classification to apply.
NOTE:
The term Data Owner is also used within Discretionary Access Control (DAC). Within DAC it means the person who has created an object. For example, if I create a file on my system then I am the owner of the file and I can decide who else could get access to the file. It is left to my discretion. Within DAC access is granted based solely on the Identity of the subject, this is why sometimes DAC is referred to as Identity Based Access Control.
The other choices were not the best answer
Running regular backups is the responsibility of custodian. Audit the data users is the responsibility of the auditors
Periodically check the validity and accuracy of the data is not one of the data owner responsibility
Reference(s) used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Page 14, Chapter 1: Security Management Practices.
NEW QUESTION 12
Which of the following standards is concerned with message handling?
- A. X.400
- B. X.500
- C. X.509
- D. X.800
Answer: A
Explanation:
X.400 is used in e-mail as a message handling protocol. X.500 is used in directory services. X.509 is used in digital certificates and X.800 is used a network security standard.
Reference: http://www.alvestrand.no/x400/.
NEW QUESTION 13
Which of the following is NOT a characteristic of a host-based intrusion detection system?
- A. A HIDS does not consume large amounts of system resources
- B. A HIDS can analyse system logs, processes and resources
- C. A HIDS looks for unauthorized changes to the system
- D. A HIDS can notify system administrators when unusual events are identified
Answer: A
Explanation:
A HIDS does not consume large amounts of system resources is the correct choice. HIDS can consume inordinate amounts of CPU and system resources in order to function effectively, especially during an event.
All the other answers are characteristics of HIDSes A HIDS can:
scrutinize event logs, critical system files, and other auditable system resources; look for unauthorized change or suspicious patterns of behavior or activity
can send alerts when unusual events are discovered
Reference:
Official guide to the CISSP CBK. Pages 197 to 198.
NEW QUESTION 14
Which layer of the OSI/ISO model handles physical addressing, network topology, line discipline, error notification, orderly delivery of frames, and optional flow control?
- A. Physical
- B. Data link
- C. Network
- D. Session
Answer: B
Explanation:
The Data Link layer provides data transport across a physical link. It handles physical addressing, network topology, line discipline, error notification, orderly delivery of frames, and optional flow control.
Source: ROTHKE, Ben, CISSP CBK Review presentation on domain 2, August 1999.
NEW QUESTION 15
Which of the following is most appropriate to notify an external user that session monitoring is being conducted?
- A. Logon Banners
- B. Wall poster
- C. Employee Handbook
- D. Written agreement
Answer: A
Explanation:
Banners at the log-on time should be used to notify external users of any monitoring that is being conducted. A good banner will give you a better legal stand and also makes it obvious the user was warned about who should access the system and if it is an unauthorized user then he is fully aware of trespassing.
This is a tricky question, the keyword in the question is External user.
There are two possible answers based on how the question is presented, this question could either apply to internal users or ANY anonymous user.
Internal users should always have a written agreement first, then logon banners serve as a constant reminder.
Anonymous users, such as those logging into a web site, ftp server or even a mail server; their only notification system is the use of a logon banner.
References used for this question:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001, John Wiley & Sons, Page 50.
and
Shon Harris, CISSP All-in-one, 5th edition, pg 873
NEW QUESTION 16
The IP header contains a protocol field. If this field contains the value of 17, what type of data is contained within the ip datagram?
- A. TCP.
- B. ICMP.
- C. UDP.
- D. IGMP.
Answer: C
Explanation:
If the protocol field has a value of 17 then it would indicate it was UDP. The following answers are incorrect answers:
TCP. Is incorrect because the value for a TCP protocol would be 6. ICMP. Is incorrect because the value for an ICMP protocol would be 1. IGMP. Is incorrect because the value for an IGMP protocol would be 2.
The protocol field of the IP packet dictates what protocol the IP packet is using. TCP=6, ICMP=1, UDP=17, IGMP=2
Reference(s) used for this question:
SANS http://www.sans.org/resources/tcpip.pdf?ref=3871
NEW QUESTION 17
Which of the following encryption algorithms does not deal with discrete logarithms?
- A. El Gamal
- B. Diffie-Hellman
- C. RSA
- D. Elliptic Curve
Answer: C
Explanation:
The security of the RSA system is based on the assumption that factoring the product into two original large prime numbers is difficult
Source:
KRUTZ, Ronald L. & VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, John Wiley & Sons, 2001, Chapter 4: Cryptography (page 159).
Shon Harris, CISSP All-in-One Examine Guide, Third Edition, McGraw-Hill Companies, August 2005, Chapter 8: Cryptography, Page 636 - 639
NEW QUESTION 18
Which of the following biometric parameters are better suited for authentication use over a long period of time?
- A. Iris pattern
- B. Voice pattern
- C. Signature dynamics
- D. Retina pattern
Answer: A
Explanation:
The iris pattern is considered lifelong. Unique features of the iris are: freckles, rings, rifts, pits, striations, fibers, filaments, furrows, vasculature and coronas. Voice, signature and retina patterns are more likely to change over time, thus are not as suitable for authentication over a long period of time without needing re-enrollment. Source: FERREL, Robert G, Questions and Answers for the CISSP Exam, domain 1 (derived from the Information Security Management Handbook, 4th Ed., by Tipton & Krause).
NEW QUESTION 19
Which of the following statements pertaining to IPSec is incorrect?
- A. IPSec can help in protecting networks from some of the IP network attacks.
- B. IPSec provides confidentiality and integrity to information transferred over IP networks through transport layer encryption and authentication.
- C. IPSec protects against man-in-the-middle attacks.
- D. IPSec protects against spoofing.
Answer: B
Explanation:
IPSec provides confidentiality and integrity to information transferred over IP networks through network (not transport) layer encryption and authentication. All other statements are correct.
Source: TIPTON, Harold F. & KRAUSE, Micki, Information Security Management Handbook, 4th edition (volume 1), 2000, CRC Press, Chapter 6, Extranet Access Control Issues (page 110).
NEW QUESTION 20
How often should a Business Continuity Plan be reviewed?
- A. At least once a month
- B. At least every six months
- C. At least once a year
- D. At least Quarterly
Answer: C
Explanation:
As stated in SP 800-34 Rev. 1:
To be effective, the plan must be maintained in a ready state that accurately reflects system requirements, procedures, organizational structure, and policies. During the Operation/Maintenance phase of the SDLC, information systems undergo frequent changes because of shifting business needs, technology upgrades, or new internal or external policies.
As a general rule, the plan should be reviewed for accuracy and completeness at an organization-defined frequency (at least once a year for the purpose of the exam) or whenever significant changes occur to any element of the plan. Certain elements, such as contact lists, will require more frequent reviews.
Remember, there could be two good answers as specified above. Either once a year or whenever significant changes occur to the plan. You will of course get only one of the two presented within you exam.
Reference(s) used for this question: NIST SP 800-34 Revision 1
NEW QUESTION 21
......
100% Valid and Newest Version SSCP Questions & Answers shared by Certleader, Get Full Dumps HERE: https://www.certleader.com/SSCP-dumps.html (New 1074 Q&As)
